Cybersecurity Patent Application Trends 2024: Difference between revisions
Appearance
Updating Cybersecurity Patent Application Trends 2024 |
Updating Cybersecurity Patent Application Trends 2024 |
||
| Line 7: | Line 7: | ||
=== Top CPC Codes === | === Top CPC Codes === | ||
* [[:Category:CPC_G06F21/602|G06F21/602]] ( | * [[:Category:CPC_G06F21/602|G06F21/602]] (No explanation available) | ||
** Count: 85 patents | ** Count: 85 patents | ||
** Example: [[20240232391. USING INQ TO OPTIMIZE END-TO-END ENCRYPTION MANAGEMENT WITH BACKUP APPLIANCES simplified abstract (EMC IP Holding Company LLC)]] | ** Example: [[20240232391. USING INQ TO OPTIMIZE END-TO-END ENCRYPTION MANAGEMENT WITH BACKUP APPLIANCES simplified abstract (EMC IP Holding Company LLC)]] | ||
* [[:Category:CPC_H04L9/008|H04L9/008]] ( | * [[:Category:CPC_H04L9/008|H04L9/008]] (No explanation available) | ||
** Count: 70 patents | ** Count: 70 patents | ||
** Example: [[20240235809. METHOD FOR HOMOMORPHIC ENCRYPTION OR DECRYPTION IN CONSIDERATION OF SPATIAL COMPLEXITY simplified abstract (CRYPTO LAB INC.)]] | ** Example: [[20240235809. METHOD FOR HOMOMORPHIC ENCRYPTION OR DECRYPTION IN CONSIDERATION OF SPATIAL COMPLEXITY simplified abstract (CRYPTO LAB INC.)]] | ||
* [[:Category:CPC_H04L63/20|H04L63/20]] ( | * [[:Category:CPC_H04L63/20|H04L63/20]] (No explanation available) | ||
** Count: 66 patents | ** Count: 66 patents | ||
** Example: [[20240236043. Signature reporting system and method simplified abstract (Sophos Limited)]] | ** Example: [[20240236043. Signature reporting system and method simplified abstract (Sophos Limited)]] | ||
* [[:Category:CPC_H04L63/0428|H04L63/0428]] ( | * [[:Category:CPC_H04L63/0428|H04L63/0428]] (No explanation available) | ||
** Count: 64 patents | ** Count: 64 patents | ||
** Example: [[20240236053. SECURE INTERFACES FOR NEURAL DEVICES simplified abstract (PRECISION NEUROSCIENCE CORPORATION)]] | ** Example: [[20240236053. SECURE INTERFACES FOR NEURAL DEVICES simplified abstract (PRECISION NEUROSCIENCE CORPORATION)]] | ||
* [[:Category:CPC_H04L63/1416|H04L63/1416]] ( | * [[:Category:CPC_H04L63/1416|H04L63/1416]] (No explanation available) | ||
** Count: 62 patents | ** Count: 62 patents | ||
** Example: [[20240236120. MANAGING AND DEPLOYING CUSTOM INTRUSION DETECTION SYSTEM SIGNATURE POLICIES simplified abstract (Visa International Service Association)]] | ** Example: [[20240236120. MANAGING AND DEPLOYING CUSTOM INTRUSION DETECTION SYSTEM SIGNATURE POLICIES simplified abstract (Visa International Service Association)]] | ||
* [[:Category:CPC_H04L9/14|H04L9/14]] ( | * [[:Category:CPC_H04L9/14|H04L9/14]] (No explanation available) | ||
** Count: 60 patents | ** Count: 60 patents | ||
** Example: [[20240235821. SYSTEMS AND METHODS FOR CONFIGURING A NETWORKED SYSTEM TO PERFORM THRESHOLD MULTI-PARTY COMPUTATION simplified abstract (PayPal, Inc.)]] | ** Example: [[20240235821. SYSTEMS AND METHODS FOR CONFIGURING A NETWORKED SYSTEM TO PERFORM THRESHOLD MULTI-PARTY COMPUTATION simplified abstract (PayPal, Inc.)]] | ||
* [[:Category:CPC_H04L63/1425|H04L63/1425]] ( | * [[:Category:CPC_H04L63/1425|H04L63/1425]] (No explanation available) | ||
** Count: 54 patents | ** Count: 54 patents | ||
** Example: [[20240236055. METHOD FOR SECURE NETWORK COMMUNICATION AND SYSTEM THEREOF simplified abstract (SAMSUNG SDS CO., LTD.)]] | ** Example: [[20240236055. METHOD FOR SECURE NETWORK COMMUNICATION AND SYSTEM THEREOF simplified abstract (SAMSUNG SDS CO., LTD.)]] | ||
* [[:Category:CPC_H04L63/1433|H04L63/1433]] ( | * [[:Category:CPC_H04L63/1433|H04L63/1433]] (No explanation available) | ||
** Count: 44 patents | ** Count: 44 patents | ||
** Example: [[20240232767. SYSTEMS AND METHODS FOR MONITORING INFORMATION SECURITY EFFECTIVENESS simplified abstract (RiskRecon Inc.)]] | ** Example: [[20240232767. SYSTEMS AND METHODS FOR MONITORING INFORMATION SECURITY EFFECTIVENESS simplified abstract (RiskRecon Inc.)]] | ||
* [[:Category:CPC_H04L9/0618|H04L9/0618]] ( | * [[:Category:CPC_H04L9/0618|H04L9/0618]] (No explanation available) | ||
** Count: 39 patents | ** Count: 39 patents | ||
** Example: [[20240235810. CRYPTOGRAPHIC PROCESSOR FOR FULLY HOMOMORPHIC ENCRYPTION (FHE) APPLICATIONS simplified abstract (THE GOVERNING COUNCIL OF THE UNIVERSITY OF TORONTO)]] | ** Example: [[20240235810. CRYPTOGRAPHIC PROCESSOR FOR FULLY HOMOMORPHIC ENCRYPTION (FHE) APPLICATIONS simplified abstract (THE GOVERNING COUNCIL OF THE UNIVERSITY OF TORONTO)]] | ||
* [[:Category:CPC_H04L9/0825|H04L9/0825]] ( | * [[:Category:CPC_H04L9/0825|H04L9/0825]] (No explanation available) | ||
** Count: 38 patents | ** Count: 38 patents | ||
** Example: [[20240235820. METHOD AND APPARATUS FOR SHARING KEYS FOR ENCRYPTION AND/OR DECRYPTION simplified abstract (Marvell Asia Pte Ltd)]] | ** Example: [[20240235820. METHOD AND APPARATUS FOR SHARING KEYS FOR ENCRYPTION AND/OR DECRYPTION simplified abstract (Marvell Asia Pte Ltd)]] | ||
| Line 44: | Line 44: | ||
* Number of Cybersecurity patents: 36 | * Number of Cybersecurity patents: 36 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_G06F12/1408|G06F12/1408]] ( | ** [[:Category:CPC_G06F12/1408|G06F12/1408]] (No explanation available): 8 patents | ||
** [[:Category:CPC_H04L9/008|H04L9/008]] ( | ** [[:Category:CPC_H04L9/008|H04L9/008]] (No explanation available): 7 patents | ||
** [[:Category:CPC_G06F21/602|G06F21/602]] ( | ** [[:Category:CPC_G06F21/602|G06F21/602]] (No explanation available): 6 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240031140. EFFICIENT LOW-OVERHEAD SIDE-CHANNEL PROTECTION FOR POLYNOMIAL MULTIPLICATION IN POST-QUANTUM ENCRYPTION simplified abstract (Intel Corporation)]] (20240125) | ** [[20240031140. EFFICIENT LOW-OVERHEAD SIDE-CHANNEL PROTECTION FOR POLYNOMIAL MULTIPLICATION IN POST-QUANTUM ENCRYPTION simplified abstract (Intel Corporation)]] (20240125) | ||
| Line 54: | Line 54: | ||
* Number of Cybersecurity patents: 16 | * Number of Cybersecurity patents: 16 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L9/0825|H04L9/0825]] ( | ** [[:Category:CPC_H04L9/0825|H04L9/0825]] (No explanation available): 3 patents | ||
** [[:Category:CPC_G06Q2220/00|G06Q2220/00]] ( | ** [[:Category:CPC_G06Q2220/00|G06Q2220/00]] (No explanation available): 3 patents | ||
** [[:Category:CPC_H04L9/0894|H04L9/0894]] ( | ** [[:Category:CPC_H04L9/0894|H04L9/0894]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240039946. CYBERSECURITY RISK ASSESSMENT AND REMEDIATION TOOL simplified abstract (Capital One Services, LLC)]] (20240201) | ** [[20240039946. CYBERSECURITY RISK ASSESSMENT AND REMEDIATION TOOL simplified abstract (Capital One Services, LLC)]] (20240201) | ||
| Line 64: | Line 64: | ||
* Number of Cybersecurity patents: 16 | * Number of Cybersecurity patents: 16 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L63/1416|H04L63/1416]] ( | ** [[:Category:CPC_H04L63/1416|H04L63/1416]] (No explanation available): 5 patents | ||
** [[:Category:CPC_G06F21/554|G06F21/554]] ( | ** [[:Category:CPC_G06F21/554|G06F21/554]] (No explanation available): 2 patents | ||
** [[:Category:CPC_G06F21/53|G06F21/53]] ( | ** [[:Category:CPC_G06F21/53|G06F21/53]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240086524. SYSTEM AND METHOD FOR AGENTLESS HOST CONFIGURATION DETECTION IN A COMPUTING ENVIRONMENT simplified abstract (Wiz, Inc.)]] (20240314) | ** [[20240086524. SYSTEM AND METHOD FOR AGENTLESS HOST CONFIGURATION DETECTION IN A COMPUTING ENVIRONMENT simplified abstract (Wiz, Inc.)]] (20240314) | ||
| Line 74: | Line 74: | ||
* Number of Cybersecurity patents: 15 | * Number of Cybersecurity patents: 15 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_G06F21/602|G06F21/602]] ( | ** [[:Category:CPC_G06F21/602|G06F21/602]] (No explanation available): 8 patents | ||
** [[:Category:CPC_G06F21/6218|G06F21/6218]] ( | ** [[:Category:CPC_G06F21/6218|G06F21/6218]] (No explanation available): 3 patents | ||
** [[:Category:CPC_G06F21/78|G06F21/78]] ( | ** [[:Category:CPC_G06F21/78|G06F21/78]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240086335. SYSTEMS AND METHODS OF SUPPORTING DEDUPLICATION AND COMPRESSION OF ENCRYPTED STORAGE VOLUMES simplified abstract (Dell Products L.P.)]] (20240314) | ** [[20240086335. SYSTEMS AND METHODS OF SUPPORTING DEDUPLICATION AND COMPRESSION OF ENCRYPTED STORAGE VOLUMES simplified abstract (Dell Products L.P.)]] (20240314) | ||
| Line 84: | Line 84: | ||
* Number of Cybersecurity patents: 14 | * Number of Cybersecurity patents: 14 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L63/1416|H04L63/1416]] ( | ** [[:Category:CPC_H04L63/1416|H04L63/1416]] (No explanation available): 3 patents | ||
** [[:Category:CPC_H04L63/083|H04L63/083]] ( | ** [[:Category:CPC_H04L63/083|H04L63/083]] (No explanation available): 2 patents | ||
** [[:Category:CPC_H04L63/1425|H04L63/1425]] ( | ** [[:Category:CPC_H04L63/1425|H04L63/1425]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240073200. INFORMATION SECURITY SYSTEM AND METHOD FOR PHISHING THREAT PREVENTION USING TOKENS simplified abstract (Bank of America Corporation)]] (20240229) | ** [[20240073200. INFORMATION SECURITY SYSTEM AND METHOD FOR PHISHING THREAT PREVENTION USING TOKENS simplified abstract (Bank of America Corporation)]] (20240229) | ||
| Line 94: | Line 94: | ||
* Number of Cybersecurity patents: 14 | * Number of Cybersecurity patents: 14 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L63/20|H04L63/20]] ( | ** [[:Category:CPC_H04L63/20|H04L63/20]] (No explanation available): 8 patents | ||
** [[:Category:CPC_H04L63/029|H04L63/029]] ( | ** [[:Category:CPC_H04L63/029|H04L63/029]] (No explanation available): 4 patents | ||
** [[:Category:CPC_H04L63/0263|H04L63/0263]] ( | ** [[:Category:CPC_H04L63/0263|H04L63/0263]] (No explanation available): 3 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240214420. APPLICATION FIREWALL simplified abstract (Sophos Limited)]] (20240627) | ** [[20240214420. APPLICATION FIREWALL simplified abstract (Sophos Limited)]] (20240627) | ||
| Line 104: | Line 104: | ||
* Number of Cybersecurity patents: 13 | * Number of Cybersecurity patents: 13 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L63/20|H04L63/20]] ( | ** [[:Category:CPC_H04L63/20|H04L63/20]] (No explanation available): 3 patents | ||
** [[:Category:CPC_H04L63/0485|H04L63/0485]] ( | ** [[:Category:CPC_H04L63/0485|H04L63/0485]] (No explanation available): 2 patents | ||
** [[:Category:CPC_H04L12/4633|H04L12/4633]] ( | ** [[:Category:CPC_H04L12/4633|H04L12/4633]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240223544. HIGH BANDWIDTH ENCRYPTION ENGINES IN A MULTIPATHING IP NETWORK simplified abstract (Cisco Technology, Inc.)]] (20240704) | ** [[20240223544. HIGH BANDWIDTH ENCRYPTION ENGINES IN A MULTIPATHING IP NETWORK simplified abstract (Cisco Technology, Inc.)]] (20240704) | ||
| Line 114: | Line 114: | ||
* Number of Cybersecurity patents: 12 | * Number of Cybersecurity patents: 12 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L9/0869|H04L9/0869]] ( | ** [[:Category:CPC_H04L9/0869|H04L9/0869]] (No explanation available): 4 patents | ||
** [[:Category:CPC_H04L9/008|H04L9/008]] ( | ** [[:Category:CPC_H04L9/008|H04L9/008]] (No explanation available): 3 patents | ||
** [[:Category:CPC_G06F13/4282|G06F13/4282]] ( | ** [[:Category:CPC_G06F13/4282|G06F13/4282]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240072992. HOMOMORPHIC ENCRYPTION OPERATOR, STORAGE DEVICE INCLUDING THE SAME, AND LEVEL CONFIGURATION METHOD THEREOF simplified abstract (Samsung Electronics Co., Ltd.)]] (20240229) | ** [[20240072992. HOMOMORPHIC ENCRYPTION OPERATOR, STORAGE DEVICE INCLUDING THE SAME, AND LEVEL CONFIGURATION METHOD THEREOF simplified abstract (Samsung Electronics Co., Ltd.)]] (20240229) | ||
| Line 124: | Line 124: | ||
* Number of Cybersecurity patents: 11 | * Number of Cybersecurity patents: 11 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_H04L63/1425|H04L63/1425]] ( | ** [[:Category:CPC_H04L63/1425|H04L63/1425]] (No explanation available): 2 patents | ||
** [[:Category:CPC_G06F21/602|G06F21/602]] ( | ** [[:Category:CPC_G06F21/602|G06F21/602]] (No explanation available): 2 patents | ||
** [[:Category:CPC_H04L9/30|H04L9/30]] ( | ** [[:Category:CPC_H04L9/30|H04L9/30]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240089100. USING A SECURE ENCLAVE TO SATISFY RETENTION AND EXPUNGEMENT REQUIREMENTS WITH RESPECT TO PRIVATE DATA simplified abstract (Microsoft Technology Licensing, LLC)]] (20240314) | ** [[20240089100. USING A SECURE ENCLAVE TO SATISFY RETENTION AND EXPUNGEMENT REQUIREMENTS WITH RESPECT TO PRIVATE DATA simplified abstract (Microsoft Technology Licensing, LLC)]] (20240314) | ||
| Line 134: | Line 134: | ||
* Number of Cybersecurity patents: 10 | * Number of Cybersecurity patents: 10 | ||
* Top CPC codes: | * Top CPC codes: | ||
** [[:Category:CPC_G06F21/64|G06F21/64]] ( | ** [[:Category:CPC_G06F21/64|G06F21/64]] (No explanation available): 2 patents | ||
** [[:Category:CPC_H04L63/0263|H04L63/0263]] ( | ** [[:Category:CPC_H04L63/0263|H04L63/0263]] (No explanation available): 2 patents | ||
** [[:Category:CPC_G06N20/00|G06N20/00]] ( | ** [[:Category:CPC_G06N20/00|G06N20/00]] (No explanation available): 2 patents | ||
* Recent patents: | * Recent patents: | ||
** [[20240098114. System and Method for Identifying and Managing Cybersecurity Top Threats simplified abstract (Google LLC)]] (20240321) | ** [[20240098114. System and Method for Identifying and Managing Cybersecurity Top Threats simplified abstract (Google LLC)]] (20240321) | ||
| Line 150: | Line 150: | ||
[[File:Emerging_Technology_Areas_in_Cybersecurity.png|border|800px]] | [[File:Emerging_Technology_Areas_in_Cybersecurity.png|border|800px]] | ||
* [[:Category:CPC_H04W76/14|H04W76/14]] ( | * [[:Category:CPC_H04W76/14|H04W76/14]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048990. BLUETOOTH CONNECTION METHOD AND SYSTEM, INTELLIGENT TERMINAL, AND COMPUTER STORAGE MEDIUM simplified abstract (SHENZHEN TCL NEW TECHNOLOGY CO., LTD.)]] | ** Example: [[20240048990. BLUETOOTH CONNECTION METHOD AND SYSTEM, INTELLIGENT TERMINAL, AND COMPUTER STORAGE MEDIUM simplified abstract (SHENZHEN TCL NEW TECHNOLOGY CO., LTD.)]] | ||
* [[:Category:CPC_H04L9/0662|H04L9/0662]] ( | * [[:Category:CPC_H04L9/0662|H04L9/0662]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048534. NETWORK SECURITY DEVICES AND METHOD simplified abstract (Wattre, Inc.)]] | ** Example: [[20240048534. NETWORK SECURITY DEVICES AND METHOD simplified abstract (Wattre, Inc.)]] | ||
* [[:Category:CPC_H04L67/52|H04L67/52]] ( | * [[:Category:CPC_H04L67/52|H04L67/52]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ||
* [[:Category:CPC_H04L61/4547|H04L61/4547]] ( | * [[:Category:CPC_H04L61/4547|H04L61/4547]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ||
* [[:Category:CPC_H04L41/0266|H04L41/0266]] ( | * [[:Category:CPC_H04L41/0266|H04L41/0266]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ||
* [[:Category:CPC_H04L41/0293|H04L41/0293]] ( | * [[:Category:CPC_H04L41/0293|H04L41/0293]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ** Example: [[20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)]] | ||
* [[:Category:CPC_H04L2209/601|H04L2209/601]] ( | * [[:Category:CPC_H04L2209/601|H04L2209/601]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048360. METHOD FOR PROCESSING MULTI-SOURCE DATA simplified abstract (JINGDONG TECHNOLOGY HOLDING CO., LTD.)]] | ** Example: [[20240048360. METHOD FOR PROCESSING MULTI-SOURCE DATA simplified abstract (JINGDONG TECHNOLOGY HOLDING CO., LTD.)]] | ||
* [[:Category:CPC_H04L67/1074|H04L67/1074]] ( | * [[:Category:CPC_H04L67/1074|H04L67/1074]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048357. SYMMETRIC ENCRYPTION FOR PRIVATE SMART CONTRACTS AMONG MULTIPLE PARTIES IN A PRIVATE PEER-TO-PEER NETWORK simplified abstract (Experian Information Solutions, Inc.)]] | ** Example: [[20240048357. SYMMETRIC ENCRYPTION FOR PRIVATE SMART CONTRACTS AMONG MULTIPLE PARTIES IN A PRIVATE PEER-TO-PEER NETWORK simplified abstract (Experian Information Solutions, Inc.)]] | ||
* [[:Category:CPC_G06F17/10|G06F17/10]] ( | * [[:Category:CPC_G06F17/10|G06F17/10]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240048353. ENCRYPTION PROCESSING DEVICE AND ENCRYPTION PROCESSING METHOD simplified abstract (AXELL CORPORATION)]] | ** Example: [[20240048353. ENCRYPTION PROCESSING DEVICE AND ENCRYPTION PROCESSING METHOD simplified abstract (AXELL CORPORATION)]] | ||
* [[:Category:CPC_G06F21/46|G06F21/46]] ( | * [[:Category:CPC_G06F21/46|G06F21/46]] (No explanation available) | ||
** Count: 1 patents | ** Count: 1 patents | ||
** Example: [[20240045972. BUILDING MANAGEMENT SYSTEM WITH CYBER HEALTH DASHBOARD simplified abstract (Johnson Controls Tyco IP Holdings LLP)]] | ** Example: [[20240045972. BUILDING MANAGEMENT SYSTEM WITH CYBER HEALTH DASHBOARD simplified abstract (Johnson Controls Tyco IP Holdings LLP)]] | ||
Revision as of 03:47, 16 July 2024
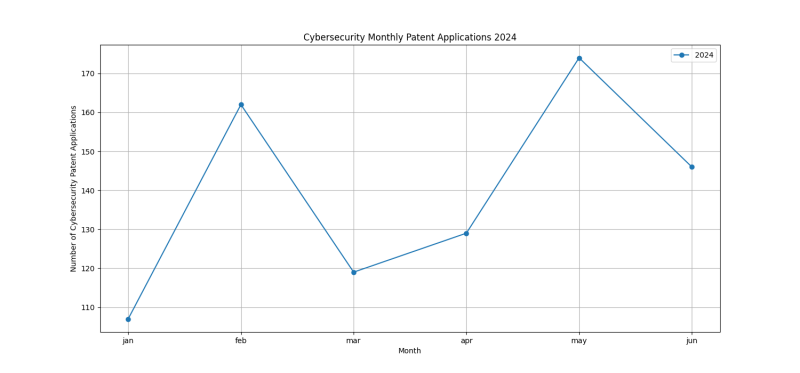
Cybersecurity Patent Application Filing Activity
Cybersecurity patent applications in 2024
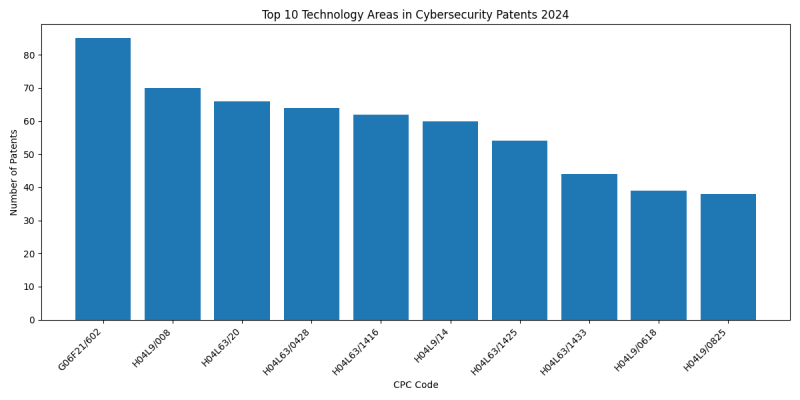
Top Technology Areas in Cybersecurity
Top CPC Codes
- G06F21/602 (No explanation available)
- H04L9/008 (No explanation available)
- H04L63/20 (No explanation available)
- Count: 66 patents
- Example: 20240236043. Signature reporting system and method simplified abstract (Sophos Limited)
- H04L63/0428 (No explanation available)
- Count: 64 patents
- Example: 20240236053. SECURE INTERFACES FOR NEURAL DEVICES simplified abstract (PRECISION NEUROSCIENCE CORPORATION)
- H04L63/1416 (No explanation available)
- H04L9/14 (No explanation available)
- H04L63/1425 (No explanation available)
- H04L63/1433 (No explanation available)
- H04L9/0618 (No explanation available)
- H04L9/0825 (No explanation available)
Top Companies in Cybersecurity
Error creating thumbnail: File missing
Intel Corporation
- Number of Cybersecurity patents: 36
- Top CPC codes:
- G06F12/1408 (No explanation available): 8 patents
- H04L9/008 (No explanation available): 7 patents
- G06F21/602 (No explanation available): 6 patents
- Recent patents:
- 20240031140. EFFICIENT LOW-OVERHEAD SIDE-CHANNEL PROTECTION FOR POLYNOMIAL MULTIPLICATION IN POST-QUANTUM ENCRYPTION simplified abstract (Intel Corporation) (20240125)
- 20240045709. SCALABLE VIRTUAL MACHINE OPERATION INSIDE TRUST DOMAINS WITHIN THE TRUST DOMAIN ARCHITECTURE simplified abstract (Intel Corporation) (20240208)
- 20240048543. ENCRYPTION ACCELERATION FOR NETWORK COMMUNICATION PACKETS simplified abstract (Intel Corporation) (20240208)
Capital One Services, LLC
- Number of Cybersecurity patents: 16
- Top CPC codes:
- H04L9/0825 (No explanation available): 3 patents
- G06Q2220/00 (No explanation available): 3 patents
- H04L9/0894 (No explanation available): 2 patents
- Recent patents:
- 20240039946. CYBERSECURITY RISK ASSESSMENT AND REMEDIATION TOOL simplified abstract (Capital One Services, LLC) (20240201)
- 20240193302. SELF-SERVICE LENDER PORTAL simplified abstract (Capital One Services, LLC) (20240613)
- 20240046266. SYSTEMS AND METHODS FOR CRYPTOGRAPHIC CONTEXT-SWITCHING AUTHENTICATION BETWEEN WEBSITE AND MOBILE DEVICE simplified abstract (Capital One Services, LLC) (20240208)
Wiz, Inc.
- Number of Cybersecurity patents: 16
- Top CPC codes:
- H04L63/1416 (No explanation available): 5 patents
- G06F21/554 (No explanation available): 2 patents
- G06F21/53 (No explanation available): 2 patents
- Recent patents:
- 20240086524. SYSTEM AND METHOD FOR AGENTLESS HOST CONFIGURATION DETECTION IN A COMPUTING ENVIRONMENT simplified abstract (Wiz, Inc.) (20240314)
- 20240089272. DETECTION OF CYBERSECURITY THREATS UTILIZING ESTABLISHED BASELINES simplified abstract (Wiz, Inc.) (20240314)
- 20240048566. LATERAL MOVEMENT ANALYSIS USING CERTIFICATE PRIVATE KEYS simplified abstract (Wiz, Inc.) (20240208)
Dell Products L.P.
- Number of Cybersecurity patents: 15
- Top CPC codes:
- G06F21/602 (No explanation available): 8 patents
- G06F21/6218 (No explanation available): 3 patents
- G06F21/78 (No explanation available): 2 patents
- Recent patents:
- 20240086335. SYSTEMS AND METHODS OF SUPPORTING DEDUPLICATION AND COMPRESSION OF ENCRYPTED STORAGE VOLUMES simplified abstract (Dell Products L.P.) (20240314)
- 20240028774. System and Method for Fabric-Independent In-Band Privacy for Security Commands on Non-volatile Memory Express Over Fabrics (NVMe-oF) simplified abstract (Dell Products L.P.) (20240125)
- 20240045981. SYSTEM AND METHOD FOR FILE RECOVERY FROM MALICIOUS ATTACKS simplified abstract (Dell Products L.P.) (20240208)
Bank of America Corporation
- Number of Cybersecurity patents: 14
- Top CPC codes:
- H04L63/1416 (No explanation available): 3 patents
- H04L63/083 (No explanation available): 2 patents
- H04L63/1425 (No explanation available): 2 patents
- Recent patents:
- 20240073200. INFORMATION SECURITY SYSTEM AND METHOD FOR PHISHING THREAT PREVENTION USING TOKENS simplified abstract (Bank of America Corporation) (20240229)
- 20240073246. INFORMATION SECURITY SYSTEM AND METHOD FOR PHISHING WEBSITE IDENTIFICATION BASED ON IMAGE HASHING simplified abstract (Bank of America Corporation) (20240229)
- 20240039935. System and method for anomaly detection for information security simplified abstract (Bank of America Corporation) (20240201)
Sophos Limited
- Number of Cybersecurity patents: 14
- Top CPC codes:
- H04L63/20 (No explanation available): 8 patents
- H04L63/029 (No explanation available): 4 patents
- H04L63/0263 (No explanation available): 3 patents
- Recent patents:
Cisco Technology, Inc.
- Number of Cybersecurity patents: 13
- Top CPC codes:
- H04L63/20 (No explanation available): 3 patents
- H04L63/0485 (No explanation available): 2 patents
- H04L12/4633 (No explanation available): 2 patents
- Recent patents:
- 20240223544. HIGH BANDWIDTH ENCRYPTION ENGINES IN A MULTIPATHING IP NETWORK simplified abstract (Cisco Technology, Inc.) (20240704)
- 20240031411. THREAT ANALYTICS AND DYNAMIC COMPLIANCE IN SECURITY POLICIES simplified abstract (Cisco Technology, Inc.) (20240125)
- 20240048384. METHOD AND APPARATUS FOR PROVIDING STRONG MUTUAL AUTHENTICATION, ENCRYPTION, AND INTEGRITY FOR CONSTRAINT DEVICES WITHOUT SECURE STORAGE AND PKI SUPPORT simplified abstract (Cisco Technology, Inc.) (20240208)
Samsung Electronics Co., Ltd.
- Number of Cybersecurity patents: 12
- Top CPC codes:
- H04L9/0869 (No explanation available): 4 patents
- H04L9/008 (No explanation available): 3 patents
- G06F13/4282 (No explanation available): 2 patents
- Recent patents:
- 20240072992. HOMOMORPHIC ENCRYPTION OPERATOR, STORAGE DEVICE INCLUDING THE SAME, AND LEVEL CONFIGURATION METHOD THEREOF simplified abstract (Samsung Electronics Co., Ltd.) (20240229)
- 20240086336. STORAGE DEVICE DELETING ENCRYPTION KEY, METHOD OF OPERATING THE SAME, AND METHOD OF OPERATING ELECTRONIC DEVICE INCLUDING THE SAME simplified abstract (Samsung Electronics Co., Ltd.) (20240314)
- 20240048354. ELECTRONIC DEVICE USING HOMOMORPHIC ENCRYPTION AND ENCRYPTED DATA PROCESSING METHOD THEREOF simplified abstract (Samsung Electronics Co., Ltd.) (20240208)
Microsoft Technology Licensing, LLC
- Number of Cybersecurity patents: 11
- Top CPC codes:
- H04L63/1425 (No explanation available): 2 patents
- G06F21/602 (No explanation available): 2 patents
- H04L9/30 (No explanation available): 2 patents
- Recent patents:
- 20240089100. USING A SECURE ENCLAVE TO SATISFY RETENTION AND EXPUNGEMENT REQUIREMENTS WITH RESPECT TO PRIVATE DATA simplified abstract (Microsoft Technology Licensing, LLC) (20240314)
- 20240220602. Virtual Environment Type Validation For Policy Enforcement simplified abstract (Microsoft Technology Licensing, LLC) (20240704)
- 20240152798. MACHINE LEARNING TRAINING DURATION CONTROL simplified abstract (Microsoft Technology Licensing, LLC) (20240509)
Google LLC
- Number of Cybersecurity patents: 10
- Top CPC codes:
- G06F21/64 (No explanation available): 2 patents
- H04L63/0263 (No explanation available): 2 patents
- G06N20/00 (No explanation available): 2 patents
- Recent patents:
- 20240098114. System and Method for Identifying and Managing Cybersecurity Top Threats simplified abstract (Google LLC) (20240321)
- 20240193309. Secure Cryptographic Coprocessor simplified abstract (Google LLC) (20240613)
- 20240089085. Fully Homomorphic Encryption Transpiler for High-level Languages simplified abstract (Google LLC) (20240314)
New Companies in Cybersecurity (Last Month)
File:New Companies in Cybersecurity Last Month.png
No new companies detected in the last month.
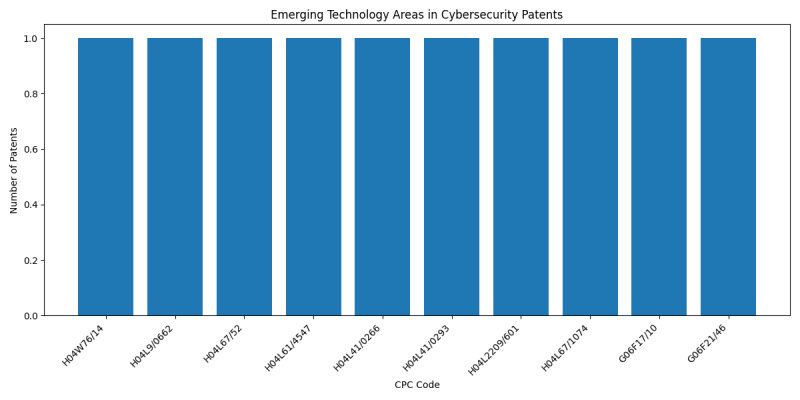
Emerging Technology Areas in Cybersecurity
- H04W76/14 (No explanation available)
- H04L9/0662 (No explanation available)
- Count: 1 patents
- Example: 20240048534. NETWORK SECURITY DEVICES AND METHOD simplified abstract (Wattre, Inc.)
- H04L67/52 (No explanation available)
- Count: 1 patents
- Example: 20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)
- H04L61/4547 (No explanation available)
- Count: 1 patents
- Example: 20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)
- H04L41/0266 (No explanation available)
- Count: 1 patents
- Example: 20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)
- H04L41/0293 (No explanation available)
- Count: 1 patents
- Example: 20240048434. TIMESTAMP-BASED ASSOCIATION OF IDENTIFIERS simplified abstract (PARRABLE INC.)
- H04L2209/601 (No explanation available)
- H04L67/1074 (No explanation available)
- G06F17/10 (No explanation available)
- G06F21/46 (No explanation available)
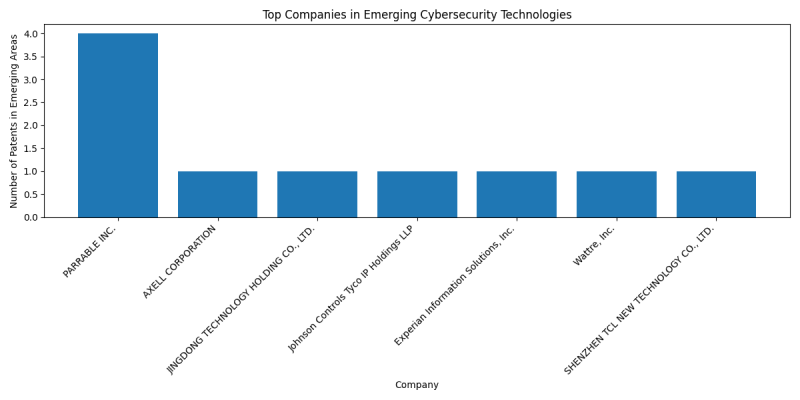
Top Companies in Emerging Cybersecurity Technologies
- PARRABLE INC.: 4 patents
- AXELL CORPORATION: 1 patents
- JINGDONG TECHNOLOGY HOLDING CO., LTD.: 1 patents
- Johnson Controls Tyco IP Holdings LLP: 1 patents
- Experian Information Solutions, Inc.: 1 patents
- Wattre, Inc.: 1 patents
- SHENZHEN TCL NEW TECHNOLOGY CO., LTD.: 1 patents