Difference between revisions of "Cybersecurity Patent Application Trends 2024"
Jump to navigation
Jump to search
Wikipatents (talk | contribs) (Updating Cybersecurity Patent Application Trends 2024) |
Wikipatents (talk | contribs) (Updating Cybersecurity Patent Application Trends 2024) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Cybersecurity Patent Application Filing Activity == | == Cybersecurity Patent Application Filing Activity == | ||
== Cybersecurity patent applications in 2024 == | == Cybersecurity patent applications in 2024 == | ||
| − | [[File:Cybersecurity_Monthly_Patent_Applications_2024_- | + | [[File:Cybersecurity_Monthly_Patent_Applications_2024_-_Up_to_November 2024.png|border|800px]] |
== Top Technology Areas in Cybersecurity == | == Top Technology Areas in Cybersecurity == | ||
| − | [[File:Top_Technology_Areas_in_Cybersecurity_2024_- | + | [[File:Top_Technology_Areas_in_Cybersecurity_2024_-_Up_to_November 2024.png|border|800px]] |
=== Top CPC Codes === | === Top CPC Codes === | ||
| − | * [[:Category: | + | * [[:Category:CPC_G06N20/00|G06N20/00]] (No explanation available) |
| − | ** Count: | + | ** Count: 1131 patents |
| − | ** Example: [[ | + | ** Example: [[20240227052. SENSOR FUSION FOR WELDING QUALITY MONITORING (Hitachi, Ltd.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G06F3/0482|G06F3/0482]] (No explanation available) |
| − | ** Count: | + | ** Count: 464 patents |
| − | ** Example: [[ | + | ** Example: [[20240231504. INTERACTION WITH A COMPUTING DEVICE VIA MOVEMENT OF A PORTION OF A USER INTERFACE (Intel Corporation)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G06N3/08|G06N3/08]] (No explanation available) |
| − | ** Count: | + | ** Count: 417 patents |
| − | ** Example: [[ | + | ** Example: [[20240230339. INTERSECTION POSE DETECTION IN AUTONOMOUS MACHINE APPLICATIONS (NVIDIA Corporation)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H04W24/10|H04W24/10]] (No explanation available) |
| − | ** Count: | + | ** Count: 367 patents |
| − | ** Example: [[ | + | ** Example: [[20240235655. METHOD AND APPARATUS FOR BEAM FAILURE RECOVERY IN A WIRELESS COMMUNICATION SYSTEM (Samsung Electronics Co., Ltd.)]] |
| − | * [[:Category:CPC_H04L63/ | + | * [[:Category:CPC_H04L63/20|H04L63/20]] (No explanation available) |
| − | ** Count: | + | ** Count: 352 patents |
| − | ** Example: [[ | + | ** Example: [[20240232407. DATA ACCESS UNDER REGULATORY CONSTRAINTS (International Business Machines Corporation)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G06T19/006|G06T19/006]] (No explanation available) |
| − | ** Count: | + | ** Count: 345 patents |
| − | ** Example: [[ | + | ** Example: [[20240226737. SOCIAL AND PROCEDURAL EFFECTS FOR COMPUTER-GENERATED ENVIRONMENTS (Warner Bros. Entertainment Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G06T2207/20081|G06T2207/20081]] (No explanation available) |
| − | ** Count: | + | ** Count: 340 patents |
| − | ** Example: [[ | + | ** Example: [[20240225536. RADIOMICS SIGNATURES FOR PATHOLOGIC CHARACTERIZATION OF STRICTURES ON MR AND CT ENTEROGRAPHY (Case Western Reserve University)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G06F3/0679|G06F3/0679]] (No explanation available) |
| − | ** Count: | + | ** Count: 340 patents |
| − | ** Example: [[ | + | ** Example: [[20240231610. CLUSTER NAMESPACE FOR A MEMORY DEVICE (Micron Technology, Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_A61K45/06|A61K45/06]] (No explanation available) |
| − | ** Count: | + | ** Count: 329 patents |
| − | ** Example: [[ | + | ** Example: [[20240226036. 2-S RIMANTADINE AND 2-R RIMANTADINE FOR TREATING CANCER (Toragen, Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H04L5/0051|H04L5/0051]] (No explanation available) |
| − | ** Count: | + | ** Count: 327 patents |
| − | ** Example: [[ | + | ** Example: [[20240235655. METHOD AND APPARATUS FOR BEAM FAILURE RECOVERY IN A WIRELESS COMMUNICATION SYSTEM (Samsung Electronics Co., Ltd.)]] |
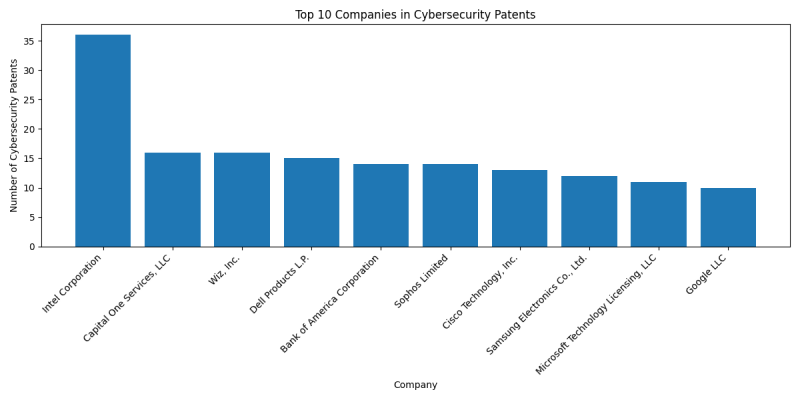
== Top Companies in Cybersecurity == | == Top Companies in Cybersecurity == | ||
[[File:Top_Companies_in_Cybersecurity.png|border|800px]] | [[File:Top_Companies_in_Cybersecurity.png|border|800px]] | ||
| − | === [[:Category: | + | === [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]] === |
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 1823 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_H04W24/10|H04W24/10]] (No explanation available): 155 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_H04L5/0051|H04L5/0051]] (No explanation available): 140 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_H04L5/0048|H04L5/0048]] (No explanation available): 108 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240049308. SYNCHRONOUS CHANNEL ACCESS CONTROL OF A WIRELESS SYSTEM (QUALCOMM Incorporated)]] (20240208) |
| − | ** [[ | + | ** [[20240049335. MANAGEMENT OF ANTENNA SWITCHING ACCORDING TO A SOUNDING REFERENCE SYMBOL ANTENNA SWITCHING CONFIGURATION (QUALCOMM Incorporated)]] (20240208) |
| − | ** [[ | + | ** [[20240049340. SMALL DATA TRANSMISSION OF NON-ACCESS STRATUM (NAS) MESSAGES AND UPLINK (UL) USER DATA PACKETS DURING A RADIO RESOURCE CONTROL (RRC) INACTIVE STATE (QUALCOMM Incorporated)]] (20240208) |
=== [[:Category:Capital One Services, LLC|Capital One Services, LLC]] === | === [[:Category:Capital One Services, LLC|Capital One Services, LLC]] === | ||
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 635 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_G06N20/00|G06N20/00]] (No explanation available): 82 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06Q20/4016|G06Q20/4016]] (No explanation available): 31 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06Q20/352|G06Q20/352]] (No explanation available): 27 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240046669. SYSTEMS AND METHODS FOR EXTRACTING IN-VIDEO MOVING TEXT IN LIVE VIDEO STREAMS (Capital One Services, LLC)]] (20240208) |
| − | ** [[ | + | ** [[20240048513. SYSTEMS AND METHODS FOR CONVERTING PHYSICAL MEETINGS INTO VIRTUAL MEETINGS (Capital One Services, LLC)]] (20240208) |
| − | ** [[ | + | ** [[20240048656. SELECTING A TARGET QUEUE FOR AN ELECTRONIC COMMUNICATION (Capital One Services, LLC)]] (20240208) |
| − | === [[:Category: | + | === [[:Category:Micron Technology, Inc.|Micron Technology, Inc.]] === |
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 631 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F3/0679|G06F3/0679]] (No explanation available): 145 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F3/0659|G06F3/0659]] (No explanation available): 101 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F3/0604|G06F3/0604]] (No explanation available): 74 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240047424. SEMICONDUCTOR DIES INCLUDING RECESSES FOR FACILITATING MECHANICAL DEBONDING, AND ASSOCIATED SYSTEMS AND DEVICES (Micron Technology, Inc.)]] (20240208) |
| − | ** [[ | + | ** [[20240047634. VERTICAL SOLID-STATE TRANSDUCERS HAVING BACKSIDE TERMINALS AND ASSOCIATED SYSTEMS AND METHODS (Micron Technology, Inc.)]] (20240208) |
| − | ** [[ | + | ** [[20240048788. INTELLIGENT INTERACTIVE VIDEO CONTENT BASED ON CONTEXTUAL AWARENESS FOR MOBILE APPLICATIONS (Micron Technology, Inc.)]] (20240208) |
| + | === [[:Category:Apple Inc.|Apple Inc.]] === | ||
| + | * Number of Cybersecurity patents: 563 | ||
| + | * Top CPC codes: | ||
| + | ** [[:Category:CPC_G06F3/013|G06F3/013]] (No explanation available): 45 patents | ||
| + | ** [[:Category:CPC_G06F3/0482|G06F3/0482]] (No explanation available): 29 patents | ||
| + | ** [[:Category:CPC_G06F3/0488|G06F3/0488]] (No explanation available): 27 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049207. Beam Management in Multi-TRP Operation (Apple Inc.)]] (20240208) | ||
| + | ** [[20240049215. Scheduling Request (SR) Enhancements for 5G Real-Time Extended Reality (XR) Services (Apple Inc.)]] (20240208) | ||
| + | ** [[20240049223. Cancellation and Replacement of PUSCH (Apple Inc.)]] (20240208) | ||
=== [[:Category:Dell Products L.P.|Dell Products L.P.]] === | === [[:Category:Dell Products L.P.|Dell Products L.P.]] === | ||
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 561 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F2201/84|G06F2201/84]] (No explanation available): 24 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F3/067|G06F3/067]] (No explanation available): 23 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F11/1451|G06F11/1451]] (No explanation available): 23 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240029462. METHOD AND SYSTEM FOR PREPROCESSING DIGITAL DOCUMENTS FOR DATA EXTRACTION (Dell Products L.P.)]] (20240125) |
| − | ** [[ | + | ** [[20240031542. INFORMATION HANDLING SYSTEM CAMERA VISUAL IMAGE COLOR TUNING BASED ON SENSED AMBIENT LIGHT COLOR (Dell Products L.P.)]] (20240125) |
| − | ** [[20240045981. SYSTEM AND METHOD FOR FILE RECOVERY FROM MALICIOUS ATTACKS | + | ** [[20240045981. SYSTEM AND METHOD FOR FILE RECOVERY FROM MALICIOUS ATTACKS (Dell Products L.P.)]] (20240208) |
| − | === [[:Category: | + | === [[:Category:Microsoft Technology Licensing, LLC|Microsoft Technology Licensing, LLC]] === |
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 464 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_G06N20/00|G06N20/00]] (No explanation available): 24 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F40/40|G06F40/40]] (No explanation available): 20 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F9/45558|G06F9/45558]] (No explanation available): 18 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240048258. HARMONIC-ENHANCED IDENTIFICATION (ID) AND DEVICE RESOLUTION FOR FREQUENCY MODULATING COMMUNICATION (Microsoft Technology Licensing, LLC)]] (20240208) |
| − | ** [[ | + | ** [[20240048447. ASSIGNMENTS OF IOT DEVICE TYPES (Microsoft Technology Licensing, LLC)]] (20240208) |
| − | ** [[ | + | ** [[20240048615. Propagating Origin Information For Applications During Application Installation (Microsoft Technology Licensing, LLC)]] (20240208) |
| − | === [[:Category: | + | === [[:Category:Google LLC|Google LLC]] === |
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 441 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_G06N20/00|G06N20/00]] (No explanation available): 25 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G10L15/22|G10L15/22]] (No explanation available): 21 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F3/0482|G06F3/0482]] (No explanation available): 18 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240048397. Identity Management for Web2 and Web3 Environments (Google LLC)]] (20240208) |
| − | ** [[ | + | ** [[20240048607. LINKS FOR WEB-BASED APPLICATIONS (Google LLC)]] (20240208) |
| − | ** [[ | + | ** [[20240048962. Method to Manage Wireless Device Profiles (Google LLC)]] (20240208) |
=== [[:Category:Cisco Technology, Inc.|Cisco Technology, Inc.]] === | === [[:Category:Cisco Technology, Inc.|Cisco Technology, Inc.]] === | ||
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 425 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category:CPC_H04L63/20|H04L63/20]] ( | + | ** [[:Category:CPC_H04L63/20|H04L63/20]] (No explanation available): 28 patents |
| − | ** [[:Category:CPC_H04L63/ | + | ** [[:Category:CPC_H04L63/1425|H04L63/1425]] (No explanation available): 19 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_H04L43/12|H04L43/12]] (No explanation available): 16 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240048562. SPONSOR DELEGATION FOR MULTI-FACTOR AUTHENTICATION (Cisco Technology, Inc.)]] (20240208) |
| − | ** [[ | + | ** [[20240049048. TRAFFIC ENGINEERING IN 5G AND LTE CUPS ARCHITECTURE (Cisco Technology, Inc.)]] (20240208) |
| − | ** [[ | + | ** [[20240049133. RESTRICTED TARGET WAIT TIME INTERFERENCE DETECTION AND MANAGEMENT (Cisco Technology, Inc.)]] (20240208) |
=== [[:Category:Samsung Electronics Co., Ltd.|Samsung Electronics Co., Ltd.]] === | === [[:Category:Samsung Electronics Co., Ltd.|Samsung Electronics Co., Ltd.]] === | ||
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 422 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_H04W24/10|H04W24/10]] (No explanation available): 23 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_H04W72/232|H04W72/232]] (No explanation available): 23 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_H04W72/23|H04W72/23]] (No explanation available): 22 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240049341. METHOD OF HANDLING ACTIVE TIME FOR SL COMMUNICATION (Samsung Electronics Co., Ltd.)]] (20240208) |
| − | ** [[ | + | ** [[20240049354. METHOD AND APPARATUS FOR LINK AND TRAFFIC LEVEL EPCS SETUP AND OPERATIONS (Samsung Electronics Co., Ltd.)]] (20240208) |
| − | ** [[ | + | ** [[20240049355. METHOD AND APPARATUS FOR OPERATION PARAMETER UPDATE FOR EPCS (Samsung Electronics Co., Ltd.)]] (20240208) |
| − | === [[:Category: | + | === [[:Category:Intel Corporation|Intel Corporation]] === |
| − | * Number of Cybersecurity patents: | + | * Number of Cybersecurity patents: 405 |
* Top CPC codes: | * Top CPC codes: | ||
| − | ** [[:Category: | + | ** [[:Category:CPC_G06T1/20|G06T1/20]] (No explanation available): 20 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F9/45558|G06F9/45558]] (No explanation available): 19 patents |
| − | ** [[:Category: | + | ** [[:Category:CPC_G06F12/1408|G06F12/1408]] (No explanation available): 14 patents |
* Recent patents: | * Recent patents: | ||
| − | ** [[ | + | ** [[20240048543. ENCRYPTION ACCELERATION FOR NETWORK COMMUNICATION PACKETS (Intel Corporation)]] (20240208) |
| − | ** [[ | + | ** [[20240048727. METHOD AND SYSTEM OF LOW LATENCY VIDEO CODING WITH INTERACTIVE APPLICATIONS (Intel Corporation)]] (20240208) |
| − | ** [[ | + | ** [[20240049272. METHODS AND DEVICES FOR RADIO RESOURCE SCHEDULING IN RADIO ACCESS NETWORKS (Intel Corporation)]] (20240208) |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== New Companies in Cybersecurity (Last Month) == | == New Companies in Cybersecurity (Last Month) == | ||
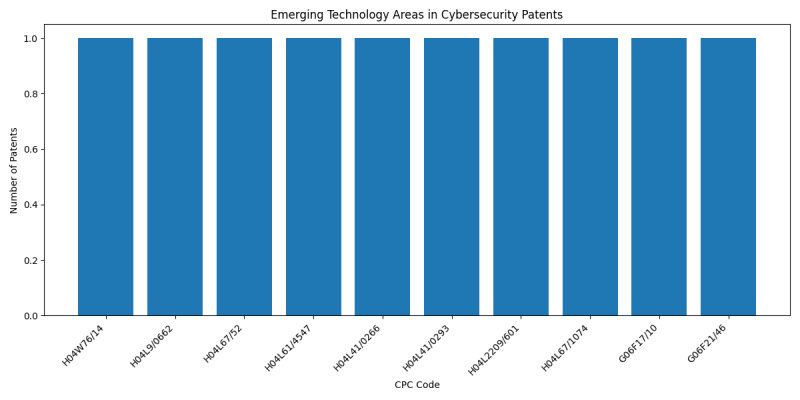
| Line 150: | Line 150: | ||
[[File:Emerging_Technology_Areas_in_Cybersecurity.png|border|800px]] | [[File:Emerging_Technology_Areas_in_Cybersecurity.png|border|800px]] | ||
| − | * [[:Category: | + | * [[:Category:CPC_H05K7/20563|H05K7/20563]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049434. Liquid cooling high-density pluggable modules for a network element (Ciena Corporation)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H05K7/20636|H05K7/20636]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049434. Liquid cooling high-density pluggable modules for a network element (Ciena Corporation)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H05B2213/07|H05B2213/07]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049369. METHODS FOR POWER CYCLE SELECTION IN APPLIANCES (Haier US Appliance Solutions, Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H05B1/0266|H05B1/0266]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049369. METHODS FOR POWER CYCLE SELECTION IN APPLIANCES (Haier US Appliance Solutions, Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H04W28/00|H04W28/00]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049298. Multicarrier Communications Employing Time Alignment Timers (Comcast Cable Communications, LLC)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H04B3/03|H04B3/03]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049209. Using Power Domain NOMA for Continuous Bandwidth Requests (Cox Communications, Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H04W36/00695|H04W36/00695]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240049071. Device, Method, Apparatus and Computer Readable Medium for Inter-Master Node Handover (Nokia Technologies OY)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G01S1/68|G01S1/68]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240048943. TRACKING DEVICE PRESENCE DETECTION AND REPORTING BY ACCESS POINTS (Tile, Inc.)]] |
| − | * [[:Category: | + | * [[:Category:CPC_H04N5/347|H04N5/347]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240048858. VIRTUAL CHANNEL CONFIGURATION SESSION OF A CAMERA SENSOR (QUALCOMM Incorporated)]] |
| − | * [[:Category: | + | * [[:Category:CPC_G01N21/9515|G01N21/9515]] (No explanation available) |
** Count: 1 patents | ** Count: 1 patents | ||
| − | ** Example: [[ | + | ** Example: [[20240048848. Optimized Path Planning for Defect Inspection based on Effective Region Coverage (Hong Kong Applied Science and Technology Resrearch Institute Company Limited)]] |
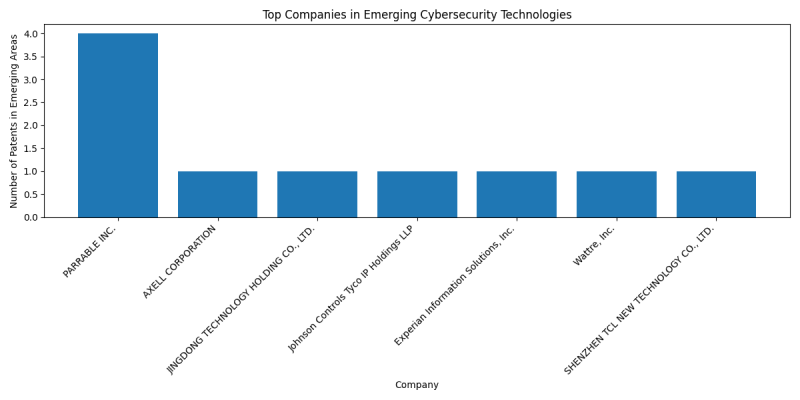
== Top Companies in Emerging Cybersecurity Technologies == | == Top Companies in Emerging Cybersecurity Technologies == | ||
[[File:Top_Companies_in_Emerging_Cybersecurity_Technologies.png|border|800px]] | [[File:Top_Companies_in_Emerging_Cybersecurity_Technologies.png|border|800px]] | ||
| − | * [[:Category: | + | * [[:Category:Haier US Appliance Solutions, Inc.|Haier US Appliance Solutions, Inc.]]: 2 patents |
| − | * [[:Category: | + | * [[:Category:Ciena Corporation|Ciena Corporation]]: 2 patents |
| − | * [[:Category: | + | * [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 1 patents |
| − | * [[:Category: | + | * [[:Category:Comcast Cable Communications, LLC|Comcast Cable Communications, LLC]]: 1 patents |
| − | * [[:Category: | + | * [[:Category:Tile, Inc.|Tile, Inc.]]: 1 patents |
| − | * [[:Category: | + | * [[:Category:Nokia Technologies OY|Nokia Technologies OY]]: 1 patents |
| − | * [[:Category: | + | * [[:Category:Cox Communications, Inc.|Cox Communications, Inc.]]: 1 patents |
| + | * [[:Category:Hong Kong Applied Science and Technology Resrearch Institute Company Limited|Hong Kong Applied Science and Technology Resrearch Institute Company Limited]]: 1 patents | ||
| + | |||
| + | == Top Inventors in Cybersecurity == | ||
| + | [[File:Top_50_Inventors_in_Cybersecurity.png|border|800px]] | ||
| + | |||
| + | === [[:Category:Tao LUO|Tao LUO of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 247 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 236 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 8 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049029. TECHNIQUES TO FACILITATE GROUP-BASED REPORTS WITH REPETITION ON CONFIGURED FOR AT LEAST ONE CHANNEL MEASUREMENT RESOURCE SET (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049239. SDCI MTRP UNIFIED TCI ACTIVATION DESIGN (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049240. UL GRANT SELECTION BY UE (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Yan ZHOU|Yan ZHOU of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 144 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 136 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 3 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 3 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048215. BEAM FAILURE DETECTION EVALUATION ON TWO TRANSMISSION CONFIGURATION INDICATOR STATES (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049029. TECHNIQUES TO FACILITATE GROUP-BASED REPORTS WITH REPETITION ON CONFIGURED FOR AT LEAST ONE CHANNEL MEASUREMENT RESOURCE SET (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049239. SDCI MTRP UNIFIED TCI ACTIVATION DESIGN (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Esmael Hejazi Dinan|Esmael Hejazi Dinan of McLean VA (US)]] === | ||
| + | * Number of Cybersecurity patents: 123 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Ofinno, LLC|Ofinno, LLC]]: 75 patents | ||
| + | ** [[:Category:Comcast Cable Communications, LLC|Comcast Cable Communications, LLC]]: 45 patents | ||
| + | ** [[:Category:Comcast Cable Communicatiions, LLC|Comcast Cable Communicatiions, LLC]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049192. TRANSMISSION AND RECEPTION CONFIGURATION AND SIGNALING (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | ** [[20240049298. Multicarrier Communications Employing Time Alignment Timers (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | ** [[20240049330. Determination of Power Control Parameters (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | === [[:Category:Xiaoxia ZHANG|Xiaoxia ZHANG of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 117 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 113 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 2 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048311. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN NON-CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048327. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049183. SIDELINK PREPARATION PROCEDURE TIME REDUCTION (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Junyi LI|Junyi LI of Fairless Hills PA (US)]] === | ||
| + | * Number of Cybersecurity patents: 110 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 106 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 2 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049183. SIDELINK PREPARATION PROCEDURE TIME REDUCTION (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049239. SDCI MTRP UNIFIED TCI ACTIVATION DESIGN (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049240. UL GRANT SELECTION BY UE (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Muhammad Sayed Khairy ABDELGHAFFAR|Muhammad Sayed Khairy ABDELGHAFFAR of San Jose CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 92 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 89 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | ** [[:Category:QUALCOM Incorporated|QUALCOM Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048308. CONFIGURATION AND INDICATION OF RESOURCES FOR PARTIAL FREQUENCY SOUNDING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048321. TIME DOMAIN ORTHOGONAL COVER CODE FOR SOUNDING REFERENCE SIGNAL TRANSMISSIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049241. TYPE 0 RESOURCE ALLOCATION IN SUB-BAND FULL-DUPLEX SLOTS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Mostafa KHOSHNEVISAN|Mostafa KHOSHNEVISAN of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 90 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 87 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 3 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048311. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN NON-CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048321. TIME DOMAIN ORTHOGONAL COVER CODE FOR SOUNDING REFERENCE SIGNAL TRANSMISSIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048327. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Peter GAAL|Peter GAAL of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 89 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 87 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049255. CONFIGURATION OF MULTICAST RECEPTION AND MOBILITY FOR USER EQUIPMENT IN AN INACTIVE STATE (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Jing SUN|Jing SUN of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 87 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 83 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 2 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048220. MANAGING BEAM SELECTION (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048301. TRANSPORT BLOCK TRANSMISSION USING DIFFERENT SPATIAL PARAMETERS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Ahmed ELSHAFIE|Ahmed ELSHAFIE of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 81 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 78 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 3 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032026. MULTIPLEXING OF OVERLAPPED UPLINK CHANNEL TRANSMISSION REPETITIONS (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240049140. COLLISION HANDLING FOR WUS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049226. CONSIDERATIONS FOR OVERLAP BETWEEN DATA AND ENERGY HARVESTING (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Alexandros MANOLAKOS|Alexandros MANOLAKOS of Escondido CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 69 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 63 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 6 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240027562. DISTRIBUTED UNIT-CENTRAL UNIT-SERVER SIGNALING OF PER-SECTOR FEATURES FOR POSITIONING (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031006. BEAM TRAINING FOR COORDINATED RELAYING (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031978. MOBILITY ANALYTICS EXCHANGE BETWEEN NETWORK ENTITIES (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Ahmed Attia ABOTABL|Ahmed Attia ABOTABL of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 69 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 69 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240049226. CONSIDERATIONS FOR OVERLAP BETWEEN DATA AND ENERGY HARVESTING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049241. TYPE 0 RESOURCE ALLOCATION IN SUB-BAND FULL-DUPLEX SLOTS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Hua Zhou|Hua Zhou of Vienna VA (US)]] === | ||
| + | * Number of Cybersecurity patents: 69 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Ofinno, LLC|Ofinno, LLC]]: 41 patents | ||
| + | ** [[:Category:Comcast Cable Communications, LLC|Comcast Cable Communications, LLC]]: 26 patents | ||
| + | ** [[:Category:Comcast Cable Communicatiions, LLC|Comcast Cable Communicatiions, LLC]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049182. Paging Early Indication (Ofinno, LLC)]] (20240208) | ||
| + | ** [[20240049192. TRANSMISSION AND RECEPTION CONFIGURATION AND SIGNALING (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | ** [[20240049330. Determination of Power Control Parameters (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | === [[:Category:Hyoungsuk Jeon|Hyoungsuk Jeon of Centreville VA (US)]] === | ||
| + | * Number of Cybersecurity patents: 68 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Ofinno, LLC|Ofinno, LLC]]: 43 patents | ||
| + | ** [[:Category:Comcast Cable Communications, LLC|Comcast Cable Communications, LLC]]: 24 patents | ||
| + | ** [[:Category:Comcast Cable Communicatiions, LLC|Comcast Cable Communicatiions, LLC]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032070. Resource Management for Multicast and Broadcast Services (Ofinno, LLC)]] (20240125) | ||
| + | ** [[20240049070. Uplink Selection For Handover (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | ** [[20240049182. Paging Early Indication (Ofinno, LLC)]] (20240208) | ||
| + | === [[:Category:Huilin XU|Huilin XU of Temecula CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 68 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 67 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240324018. BEAM SELECTION FOR RANDOM ACCESS IN A HIERARCHICAL BEAM ARCHITECTURE (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240049140. COLLISION HANDLING FOR WUS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049232. JOINT ADAPTATION BETWEEN CONTROL CHANNELS AND OTHER CONFIGURATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Kevin Higgins|Kevin Higgins of Reno NV (US)]] === | ||
| + | * Number of Cybersecurity patents: 65 | ||
| + | * Top companies: | ||
| + | ** [[:Category:IGT|IGT]]: 65 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240046753. NON-FUNGIBLE TOKENS IN GAMING (IGT)]] (20240208) | ||
| + | ** [[20240046754. GAMING SYSTEM, DEVICE, AND METHOD TO TRACK ELECTRONIC TICKETS AND VALUES THEREOF (IGT)]] (20240208) | ||
| + | ** [[20240046755. NON-FUNGIBLE TOKENS IN GAMING (IGT)]] (20240208) | ||
| + | === [[:Category:Ali Cagatay Cirik|Ali Cagatay Cirik of Chantilly VA (US)]] === | ||
| + | * Number of Cybersecurity patents: 63 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Ofinno, LLC|Ofinno, LLC]]: 37 patents | ||
| + | ** [[:Category:Comcast Cable Communications, LLC|Comcast Cable Communications, LLC]]: 24 patents | ||
| + | ** [[:Category:Comcast Cable Communicatiions, LLC|Comcast Cable Communicatiions, LLC]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049182. Paging Early Indication (Ofinno, LLC)]] (20240208) | ||
| + | ** [[20240049192. TRANSMISSION AND RECEPTION CONFIGURATION AND SIGNALING (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | ** [[20240049330. Determination of Power Control Parameters (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | === [[:Category:Wanshi CHEN|Wanshi CHEN of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 61 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 58 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049140. COLLISION HANDLING FOR WUS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Yu ZHANG|Yu ZHANG of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 61 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 52 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 9 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048214. TECHNIQUES FOR COMMUNICATING USING A RECONFIGURABLE SURFACE (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048308. CONFIGURATION AND INDICATION OF RESOURCES FOR PARTIAL FREQUENCY SOUNDING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049015. TECHNIQUES FOR REPORTING CHANNEL STATE INFORMATION (QUALCOMM INCORPORATED)]] (20240208) | ||
| + | === [[:Category:Sony AKKARAKARAN|Sony AKKARAKARAN of Poway CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 60 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 55 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 4 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031991. NETWORK INDICATION TO CONTROL SIDELINK BEAM SELECTION (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240032061. DOWNLINK CONTROL INFORMATION BASED UNIFIED TRANSMISSION CONFIGURATION INDICATOR ACKNOWLEDGEMENT (QUALCOMM INCORPORATED)]] (20240125) | ||
| + | ** [[20240048175. COMB OFFSET HOPPING FOR SRS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Hung Dinh LY|Hung Dinh LY of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 59 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 54 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 5 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240324025. RESOURCE MAPPING FOR RANDOM ACCESS REPETITIONS USING A SAME SPATIAL FILTER (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240031897. PHYSICAL UPLINK SHARED CHANNEL REPETITIONS DURING HANDOVER (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240048214. TECHNIQUES FOR COMMUNICATING USING A RECONFIGURABLE SURFACE (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Sarbajit K. Rakshit|Sarbajit K. Rakshit]] === | ||
| + | * Number of Cybersecurity patents: 58 | ||
| + | * Top companies: | ||
| + | ** [[:Category:International Business Machines Corporation|International Business Machines Corporation]]: 29 patents | ||
| + | ** [[:Category:INTERNATIONAL BUSINESS MACHINES CORPORATION|INTERNATIONAL BUSINESS MACHINES CORPORATION]]: 28 patents | ||
| + | ** [[:Category:Maplebear Inc.|Maplebear Inc.]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240223857. PERFORMING CONTEXT BASED DELIVERY OF DIGITAL CONTENT (International Business Machines Corporation)]] (20240704) | ||
| + | ** [[20240152152. Collaborative Capability Enhancement Among Machines (International Business Machines Corporation)]] (20240509) | ||
| + | ** [[20240331025. DYNAMIC BIDDING IN VIRTUAL COLLABORATIVE DOMAIN (International Business Machines Corporation)]] (20241003) | ||
| + | === [[:Category:Kyungmin Park|Kyungmin Park of Vienna VA (US)]] === | ||
| + | * Number of Cybersecurity patents: 58 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Ofinno, LLC|Ofinno, LLC]]: 36 patents | ||
| + | ** [[:Category:Comcast Cable Communications, LLC|Comcast Cable Communications, LLC]]: 20 patents | ||
| + | ** [[:Category:Comcast Cable Communicatiions, LLC|Comcast Cable Communicatiions, LLC]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240323868. Physical Channel Processing Capability for Multiple Transmission Reception Points (Ofinno, LLC)]] (20240926) | ||
| + | ** [[20240324046. Beam Management for Cells in Wireless Communications (Comcast Cable Communications, LLC)]] (20240926) | ||
| + | ** [[20240049070. Uplink Selection For Handover (Comcast Cable Communications, LLC)]] (20240208) | ||
| + | === [[:Category:Srinivas YERRAMALLI|Srinivas YERRAMALLI of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 57 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 57 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031978. MOBILITY ANALYTICS EXCHANGE BETWEEN NETWORK ENTITIES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240048220. MANAGING BEAM SELECTION (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Tao Luo|Tao Luo of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 57 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 49 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 6 patents | ||
| + | ** [[:Category:QUALCOMM lncorporated|QUALCOMM lncorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032023. REFERENCE SIGNAL PORT ASSOCIATION DETERMINATION FOR SINGLE FREQUENCY NETWORK UPLINK (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240049088. MOBILITY OPTIMIZATION FOR NETWORK ENERGY SAVING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049269. WAVEFORM-SPECIFIC TRANSMISSION PARTS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Dawei Zhang|Dawei Zhang of Saratoga CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 57 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Apple Inc.|Apple Inc.]]: 46 patents | ||
| + | ** [[:Category:APPLE INC.|APPLE INC.]]: 9 patents | ||
| + | ** [[:Category:Apple Inc|Apple Inc]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031102. LAYER-1 REFERENCE SIGNALING OUTSIDE OF CARRIER BANDWIDTHS (Apple Inc.)]] (20240125) | ||
| + | ** [[20240049215. Scheduling Request (SR) Enhancements for 5G Real-Time Extended Reality (XR) Services (Apple Inc.)]] (20240208) | ||
| + | ** [[20240049223. Cancellation and Replacement of PUSCH (Apple Inc.)]] (20240208) | ||
| + | === [[:Category:Alberto RICO ALVARINO|Alberto RICO ALVARINO of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 57 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 56 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240049062. GROUP HANDOVER CONFIGURATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049255. CONFIGURATION OF MULTICAST RECEPTION AND MOBILITY FOR USER EQUIPMENT IN AN INACTIVE STATE (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Shan LIU|Shan LIU of San Jose CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 56 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Tencent America LLC|Tencent America LLC]]: 44 patents | ||
| + | ** [[:Category:TENCENT AMERICA LLC|TENCENT AMERICA LLC]]: 12 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031577. MOTION VECTOR PREDICTION FUSION FOR SUBBLOCK-BASED TEMPORAL MOTION VECTOR PREDICTION (SbTMVP) AND TEMPORAL MOTION VECTOR PREDICTION (TMVP) (TENCENT AMERICA LLC)]] (20240125) | ||
| + | ** [[20240031592. TEMPORAL MOTION VECTOR PREDICTOR WITH DISPLACEMENT (TENCENT AMERICA LLC)]] (20240125) | ||
| + | ** [[20240031594. METHOD AND APPARATUS FOR INTER PREDICTION MODE DEPENDENT SCALING FACTORS (TENCENT AMERICA LLC)]] (20240125) | ||
| + | === [[:Category:Hao XU|Hao XU]] === | ||
| + | * Number of Cybersecurity patents: 54 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 48 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 6 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048209. MULTI-MODE PRECODING MATRIX INFORMATION REPORT FOR ORBITAL ANGULAR MOMENTUM BASED COMMUNICATION SYSTEM (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049015. TECHNIQUES FOR REPORTING CHANNEL STATE INFORMATION (QUALCOMM INCORPORATED)]] (20240208) | ||
| + | ** [[20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Qian ZHANG|Qian ZHANG of Basking Ridge NJ (US)]] === | ||
| + | * Number of Cybersecurity patents: 54 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 52 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | ** [[:Category:QUALCOM Incorporated|QUALCOM Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240334220. CROSS-LINK INTERFERENCE MEASUREMENT (QUALCOMM Incorporated)]] (20241003) | ||
| + | ** [[20240323729. MEASURING UE CLI MEASUREMENT TIMING ADJUSTMENT (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240031840. TECHNIQUES FOR AUTONOMOUS SELF-INTERFERENCE MEASUREMENTS (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Fang YUAN|Fang YUAN]] === | ||
| + | * Number of Cybersecurity patents: 54 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 49 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 4 patents | ||
| + | ** [[:Category:QUALCOMM incorporated|QUALCOMM incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032061. DOWNLINK CONTROL INFORMATION BASED UNIFIED TRANSMISSION CONFIGURATION INDICATOR ACKNOWLEDGEMENT (QUALCOMM INCORPORATED)]] (20240125) | ||
| + | ** [[20240032133. UNIFIED TRANSMISSION CONFIGURATION INDICATION FOR NONDEDICATED CHANNELS (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240048215. BEAM FAILURE DETECTION EVALUATION ON TWO TRANSMISSION CONFIGURATION INDICATOR STATES (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Jeremy R. Fox|Jeremy R. Fox of Georgetown TX (US)]] === | ||
| + | * Number of Cybersecurity patents: 53 | ||
| + | * Top companies: | ||
| + | ** [[:Category:International Business Machines Corporation|International Business Machines Corporation]]: 27 patents | ||
| + | ** [[:Category:INTERNATIONAL BUSINESS MACHINES CORPORATION|INTERNATIONAL BUSINESS MACHINES CORPORATION]]: 26 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240331025. DYNAMIC BIDDING IN VIRTUAL COLLABORATIVE DOMAIN (International Business Machines Corporation)]] (20241003) | ||
| + | ** [[20240316465. MULTIPLAYER E-GAMING IMPORTABLE CONTROLS AND SETTINGS (INTERNATIONAL BUSINESS MACHINES CORPORATION)]] (20240926) | ||
| + | ** [[20240321270. VIRTUAL ASSISTANT NOTIFICATION AMELIORATION AND AWARENESS SYSTEMS AND METHODS (International Business Machines Corporation)]] (20240926) | ||
| + | === [[:Category:Navid ABEDINI|Navid ABEDINI of Basking Ridge NJ (US)]] === | ||
| + | * Number of Cybersecurity patents: 52 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 50 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240027569. COOPERATIVE MEASUREMENT BY CO-LOCATED DEVICES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031840. TECHNIQUES FOR AUTONOMOUS SELF-INTERFERENCE MEASUREMENTS (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031849. ACCESS CONTROL FOR NETWORK ENERGY SAVINGS (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Linhai HE|Linhai HE of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 52 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 50 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240333405. CONFIGURATION AND PROCEDURE FOR SEARCH SPACE USED IN SMALL DATA TRANSFER OVER PRE-CONFIGURED UPLINK RESOURCES (QUALCOMM Incorporated)]] (20241003) | ||
| + | ** [[20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240049232. JOINT ADAPTATION BETWEEN CONTROL CHANNELS AND OTHER CONFIGURATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Kapil GULATI|Kapil GULATI of Belle Mead NJ (US)]] === | ||
| + | * Number of Cybersecurity patents: 49 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 43 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 3 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 3 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240027569. COOPERATIVE MEASUREMENT BY CO-LOCATED DEVICES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031889. MODE 1 NETWORK ENTITY INITIATED NETWORK CODING HANDOVER (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031954. SYNCHRONIZED LONG RANGE SIDELINK COMMUNICATION (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Wooseok NAM|Wooseok NAM of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 47 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 45 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048977. DATA SIGNATURES FOR ML SECURITY (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049232. JOINT ADAPTATION BETWEEN CONTROL CHANNELS AND OTHER CONFIGURATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049240. UL GRANT SELECTION BY UE (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Chunxuan Ye|Chunxuan Ye of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 44 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Apple Inc.|Apple Inc.]]: 28 patents | ||
| + | ** [[:Category:APPLE INC.|APPLE INC.]]: 9 patents | ||
| + | ** [[:Category:InterDigital Patent Holdings, Inc.|InterDigital Patent Holdings, Inc.]]: 5 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031079. METHODS FOR MULTI-PDSCH TRANSMISSION WITH MULTIPLE PUCCH RESOURCES (APPLE INC.)]] (20240125) | ||
| + | ** [[20240049215. Scheduling Request (SR) Enhancements for 5G Real-Time Extended Reality (XR) Services (Apple Inc.)]] (20240208) | ||
| + | ** [[20240049223. Cancellation and Replacement of PUSCH (Apple Inc.)]] (20240208) | ||
| + | === [[:Category:Abdelrahman Mohamed Ahmed Mohamed IBRAHIM|Abdelrahman Mohamed Ahmed Mohamed IBRAHIM of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 44 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 43 patents | ||
| + | ** [[:Category:QUALCOM Incorporated|QUALCOM Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240322989. TECHNIQUES FOR SUB-BAND FULL-DUPLEX MODE AWARE COMMUNICATION (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240049241. TYPE 0 RESOURCE ALLOCATION IN SUB-BAND FULL-DUPLEX SLOTS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Ahmed Attia Abotabl|Ahmed Attia Abotabl of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 43 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 43 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032001. FREQUENCY HOPPING IN FULL-DUPLEX COMMUNICATIONS (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240048343. ADAPTATION OF A FIRST AVAILABLE RESOURCE BLOCK AND RESOURCE BLOCK GROUP SIZE FOR FULL-DUPLEX COMMUNICATIONS (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049002. MULTIPLE SEQUENCES OF NETWORK OPERATIONS FOR MULTIPLE TRANSMISSION AND RECEPTION POINTS (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Paul Marinier|Paul Marinier]] === | ||
| + | * Number of Cybersecurity patents: 43 | ||
| + | * Top companies: | ||
| + | ** [[:Category:InterDigital Patent Holdings, Inc.|InterDigital Patent Holdings, Inc.]]: 39 patents | ||
| + | ** [[:Category:INTERDIGITAL PATENT HOLDINGS, INC.|INTERDIGITAL PATENT HOLDINGS, INC.]]: 4 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240224320. SIMULTANEOUS UPLINK AND SIDELINK OPERATION (InterDigital Patent Holdings, Inc.)]] (20240704) | ||
| + | ** [[20240322979. METHODS FOR ULTRA-RELIABLE LOW-LATENCY COMMUNICATION MULTIPLEXING (INTERDIGITAL PATENT HOLDINGS, INC.)]] (20240926) | ||
| + | ** [[20240323922. SYSTEMS AND METHODS FOR SIDELINK COMMUNICATION (InterDigital Patent Holdings, Inc.)]] (20240926) | ||
| + | === [[:Category:Marwen ZORGUI|Marwen ZORGUI of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 42 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 42 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240323842. CELL WAKE-UP SIGNAL TRIGGERING AND RESOURCE SELECTION (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240323891. POSITIONING MODEL CAPABILITY CONFIGURATION (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240323988. CONFLICT RESOLUTION BETWEEN DATA TRANSMISSIONS AND NON-DATA SERVICE SIGNALS (QUALCOMM Incorporated)]] (20240926) | ||
| + | === [[:Category:Joshua EDWARDS|Joshua EDWARDS of Philadelphia PA (US)]] === | ||
| + | * Number of Cybersecurity patents: 42 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Capital One Services, LLC|Capital One Services, LLC]]: 40 patents | ||
| + | ** [[:Category:Capital One Servies, LLC|Capital One Servies, LLC]]: 1 patents | ||
| + | ** [[:Category:Capital One Services,LLC|Capital One Services,LLC]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240029142. METHODS AND SYSTEMS FOR ANONYMIZING AND PROVIDING ACCESS TO TRANSACTION DATA (Capital One Services, LLC)]] (20240125) | ||
| + | ** [[20240046270. INTELLIGENT DECISIONING AND ROUTING FOR REQUESTS RELATED TO AUTOMATED EVENTS (Capital One Services, LLC)]] (20240208) | ||
| + | ** [[20240046298. SYSTEMS AND METHODS FOR PROMOTING TRANSACTION REWARDS (Capital One Services, LLC)]] (20240208) | ||
| + | === [[:Category:Jelena DAMNJANOVIC|Jelena DAMNJANOVIC of Del Mar CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 42 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 42 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240155719. UPLINK CHANNEL TRANSMISSIONS USING PER-TRANSMIT-RECEIVE-POINT-AND-PANEL POWER CONTROL PARAMETERS (QUALCOMM Incorporated)]] (20240509) | ||
| + | ** [[20240334399. SIDELINK BEAM MANAGEMENT BASED ON REFERENCE SIGNAL AND SIDELINK CHANNEL TRANSMISSIONS (QUALCOMM Incorporated)]] (20241003) | ||
| + | ** [[20240031895. JOINT TIMING ADVANCE AND CELL ACTIVATION SIGNALING (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Weimin DUAN|Weimin DUAN of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 40 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 38 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 2 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240319359. RECONFIGURABLE INTELLIGENT SURFACE (RIS) AIDED ROUND-TRIP-TIME (RTT)-BASED USER EQUIPMENT (UE) POSITIONING (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240027562. DISTRIBUTED UNIT-CENTRAL UNIT-SERVER SIGNALING OF PER-SECTOR FEATURES FOR POSITIONING (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240031823. BEAM ADAPTATION FOR RECONFIGURABLE INTELLIGENT SURFACE AIDED UE POSITIONING (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Krishna Kiran MUKKAVILLI|Krishna Kiran MUKKAVILLI of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 40 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 34 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 6 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated)]] (20240125) | ||
| + | ** [[20240048214. TECHNIQUES FOR COMMUNICATING USING A RECONFIGURABLE SURFACE (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240048945. SELECTIVE TRIGGERING OF NEURAL NETWORK FUNCTIONS FOR POSITIONING MEASUREMENT FEATURE PROCESSING AT A USER EQUIPMENT (QUALCOMM Incorporated)]] (20240208) | ||
| + | === [[:Category:Jeffrey RULE|Jeffrey RULE of Chevy Chase MD (US)]] === | ||
| + | * Number of Cybersecurity patents: 40 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Capital One Services, LLC|Capital One Services, LLC]]: 40 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031477. MACHINE LEARNING DATASET GENERATION USING A NATURAL LANGUAGE PROCESSING TECHNIQUE (Capital One Services, LLC)]] (20240125) | ||
| + | ** [[20240045939. STEGANOGRAPHIC IMAGE ENCODING OF BIOMETRIC TEMPLATE INFORMATION ON A CARD (Capital One Services, LLC)]] (20240208) | ||
| + | ** [[20240046266. SYSTEMS AND METHODS FOR CRYPTOGRAPHIC CONTEXT-SWITCHING AUTHENTICATION BETWEEN WEBSITE AND MOBILE DEVICE (Capital One Services, LLC)]] (20240208) | ||
| + | === [[:Category:Ahmed Elshafie|Ahmed Elshafie of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 40 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 35 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 4 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240224276. ADVANCED CODING FOR UPLINK AND DOWNLINK TRANSMISSIONS (QUALCOMM Incorporated)]] (20240704) | ||
| + | ** [[20240155432. TECHNIQUES FOR INTER-CELL TRAFFIC COORDINATION (QUALCOMM Incorporated)]] (20240509) | ||
| + | ** [[20240323731. PREEMPTION OF CROSS LINK INTERFERENCE RESOURCE (Qualcomm Incorporated)]] (20240926) | ||
| + | === [[:Category:Gabi SARKIS|Gabi SARKIS of San Diego CA (US)]] === | ||
| + | * Number of Cybersecurity patents: 40 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 38 patents | ||
| + | ** [[:Category:Qualcomm Incorporated|Qualcomm Incorporated]]: 1 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240333585. RESOURCE SELECTION FOR SELF-CONTAINED INTER-USER-EQUIPMENT COORDINATION MESSAGE (QUALCOMM Incorporated)]] (20241003) | ||
| + | ** [[20240323893. SIDELINK POSITIONING ANCHOR CLASSIFICATION AND SELECTION (QUALCOMM Incorporated)]] (20240926) | ||
| + | ** [[20240031889. MODE 1 NETWORK ENTITY INITIATED NETWORK CODING HANDOVER (QUALCOMM Incorporated)]] (20240125) | ||
| + | === [[:Category:Yushu Zhang|Yushu Zhang]] === | ||
| + | * Number of Cybersecurity patents: 38 | ||
| + | * Top companies: | ||
| + | ** [[:Category:Apple Inc.|Apple Inc.]]: 26 patents | ||
| + | ** [[:Category:APPLE INC.|APPLE INC.]]: 12 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240031096. SOLUTIONS FOR ENHANCEMENT OF INTER-CELL OPERATION FOR MULTI-TRP (APPLE INC.)]] (20240125) | ||
| + | ** [[20240032054. ENHANCEMENT ON SCHEDULING AND HARQ-ACK FEEDBACK FOR URLLC, MULTIPLEXING SCHEME FOR CONTROL/DATA CHANNEL AND DM-RS FOR NR, AND ACTIVATION MECHANISM, SCHEDULING ASPECTS, AND SYNCHRONIZATION SIGNAL (SS) BLOCKS FOR NEW RADIO (NR) SYSTEM WITH MULTIPLE BANDWIDTH PARTS (BWPS) (Apple Inc.)]] (20240125) | ||
| + | ** [[20240032055. ENHANCEMENT ON SCHEDULING AND HARQ-ACK FEEDBACK FOR URLLC, MULTIPLEXING SCHEME FOR CONTROL/DATA CHANNEL AND DM-RS FOR NR, AND ACTIVATION MECHANISM, SCHEDULING ASPECTS, AND SYNCHRONIZATION SIGNAL (SS) BLOCKS FOR NEW RADIO (NR) SYSTEM WITH MULTIPLE BANDWIDTH PARTS (BWPS) (Apple Inc.)]] (20240125) | ||
| + | === [[:Category:Kazuki TAKEDA|Kazuki TAKEDA]] === | ||
| + | * Number of Cybersecurity patents: 38 | ||
| + | * Top companies: | ||
| + | ** [[:Category:QUALCOMM Incorporated|QUALCOMM Incorporated]]: 37 patents | ||
| + | ** [[:Category:QUALCOMM INCORPORATED|QUALCOMM INCORPORATED]]: 1 patents | ||
| + | * Recent patents: | ||
| + | ** [[20240048297. HYBRID AUTOMATIC REPEAT REQUEST PROCESS SPACE MANAGEMENT FOR MULTI-CELL SCHEDULING (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated)]] (20240208) | ||
| + | ** [[20240049255. CONFIGURATION OF MULTICAST RECEPTION AND MOBILITY FOR USER EQUIPMENT IN AN INACTIVE STATE (QUALCOMM Incorporated)]] (20240208) | ||
| + | |||
| + | == Top Collaborations in Cybersecurity == | ||
| + | [[File:Top_20_Collaborations_in_Cybersecurity.png|border|800px]] | ||
| + | |||
| + | == Top US States for Cybersecurity Inventors == | ||
| + | [[File:Top_10_US_States_for_Cybersecurity_Inventors.png|border|800px]] | ||
| + | |||
| + | |||
| + | == Top Cities for Cybersecurity Inventors == | ||
| + | [[File:Top_20_Cities_for_Cybersecurity_Inventors.png|border|800px]] | ||
| + | |||
| + | * San Diego: 6594 inventors | ||
| + | * San Jose: 3707 inventors | ||
| + | * San Francisco: 3459 inventors | ||
| + | * Beijing: 3087 inventors | ||
| + | * Bangalore: 2611 inventors | ||
| + | * Tokyo: 1882 inventors | ||
| + | * Shanghai: 1736 inventors | ||
| + | * New York: 1485 inventors | ||
| + | * Seattle: 1407 inventors | ||
| + | * Sunnyvale: 1323 inventors | ||
| + | * Shenzhen: 1272 inventors | ||
| + | * Austin: 1243 inventors | ||
| + | * Mountain View: 1232 inventors | ||
| + | * Cambridge: 1159 inventors | ||
| + | * London: 1086 inventors | ||
| + | * Santa Clara: 1045 inventors | ||
| + | * Palo Alto: 999 inventors | ||
| + | * Suwon-si: 933 inventors | ||
| + | * Fremont: 882 inventors | ||
| + | * Seoul: 878 inventors | ||
[[Category:Cybersecurity]] | [[Category:Cybersecurity]] | ||
[[Category:Patent Application Trends by Technology in 2024]] | [[Category:Patent Application Trends by Technology in 2024]] | ||
Latest revision as of 04:07, 23 December 2024
Contents
- 1 Cybersecurity Patent Application Filing Activity
- 2 Cybersecurity patent applications in 2024
- 3 Top Technology Areas in Cybersecurity
- 4 Top Companies in Cybersecurity
- 5 New Companies in Cybersecurity (Last Month)
- 6 Emerging Technology Areas in Cybersecurity
- 7 Top Companies in Emerging Cybersecurity Technologies
- 8 Top Inventors in Cybersecurity
- 8.1 Tao LUO of San Diego CA (US)
- 8.2 Yan ZHOU of San Diego CA (US)
- 8.3 Esmael Hejazi Dinan of McLean VA (US)
- 8.4 Xiaoxia ZHANG of San Diego CA (US)
- 8.5 Junyi LI of Fairless Hills PA (US)
- 8.6 Muhammad Sayed Khairy ABDELGHAFFAR of San Jose CA (US)
- 8.7 Mostafa KHOSHNEVISAN of San Diego CA (US)
- 8.8 Peter GAAL of San Diego CA (US)
- 8.9 Jing SUN of San Diego CA (US)
- 8.10 Ahmed ELSHAFIE of San Diego CA (US)
- 8.11 Alexandros MANOLAKOS of Escondido CA (US)
- 8.12 Ahmed Attia ABOTABL of San Diego CA (US)
- 8.13 Hua Zhou of Vienna VA (US)
- 8.14 Hyoungsuk Jeon of Centreville VA (US)
- 8.15 Huilin XU of Temecula CA (US)
- 8.16 Kevin Higgins of Reno NV (US)
- 8.17 Ali Cagatay Cirik of Chantilly VA (US)
- 8.18 Wanshi CHEN of San Diego CA (US)
- 8.19 Yu ZHANG of San Diego CA (US)
- 8.20 Sony AKKARAKARAN of Poway CA (US)
- 8.21 Hung Dinh LY of San Diego CA (US)
- 8.22 Sarbajit K. Rakshit
- 8.23 Kyungmin Park of Vienna VA (US)
- 8.24 Srinivas YERRAMALLI of San Diego CA (US)
- 8.25 Tao Luo of San Diego CA (US)
- 8.26 Dawei Zhang of Saratoga CA (US)
- 8.27 Alberto RICO ALVARINO of San Diego CA (US)
- 8.28 Shan LIU of San Jose CA (US)
- 8.29 Hao XU
- 8.30 Qian ZHANG of Basking Ridge NJ (US)
- 8.31 Fang YUAN
- 8.32 Jeremy R. Fox of Georgetown TX (US)
- 8.33 Navid ABEDINI of Basking Ridge NJ (US)
- 8.34 Linhai HE of San Diego CA (US)
- 8.35 Kapil GULATI of Belle Mead NJ (US)
- 8.36 Wooseok NAM of San Diego CA (US)
- 8.37 Chunxuan Ye of San Diego CA (US)
- 8.38 Abdelrahman Mohamed Ahmed Mohamed IBRAHIM of San Diego CA (US)
- 8.39 Ahmed Attia Abotabl of San Diego CA (US)
- 8.40 Paul Marinier
- 8.41 Marwen ZORGUI of San Diego CA (US)
- 8.42 Joshua EDWARDS of Philadelphia PA (US)
- 8.43 Jelena DAMNJANOVIC of Del Mar CA (US)
- 8.44 Weimin DUAN of San Diego CA (US)
- 8.45 Krishna Kiran MUKKAVILLI of San Diego CA (US)
- 8.46 Jeffrey RULE of Chevy Chase MD (US)
- 8.47 Ahmed Elshafie of San Diego CA (US)
- 8.48 Gabi SARKIS of San Diego CA (US)
- 8.49 Yushu Zhang
- 8.50 Kazuki TAKEDA
- 9 Top Collaborations in Cybersecurity
- 10 Top US States for Cybersecurity Inventors
- 11 Top Cities for Cybersecurity Inventors
Cybersecurity Patent Application Filing Activity
Cybersecurity patent applications in 2024
Top Technology Areas in Cybersecurity
Top CPC Codes
- G06N20/00 (No explanation available)
- Count: 1131 patents
- Example: 20240227052. SENSOR FUSION FOR WELDING QUALITY MONITORING (Hitachi, Ltd.)
- G06F3/0482 (No explanation available)
- G06N3/08 (No explanation available)
- Count: 417 patents
- Example: 20240230339. INTERSECTION POSE DETECTION IN AUTONOMOUS MACHINE APPLICATIONS (NVIDIA Corporation)
- H04W24/10 (No explanation available)
- H04L63/20 (No explanation available)
- Count: 352 patents
- Example: 20240232407. DATA ACCESS UNDER REGULATORY CONSTRAINTS (International Business Machines Corporation)
- G06T19/006 (No explanation available)
- Count: 345 patents
- Example: 20240226737. SOCIAL AND PROCEDURAL EFFECTS FOR COMPUTER-GENERATED ENVIRONMENTS (Warner Bros. Entertainment Inc.)
- G06T2207/20081 (No explanation available)
- G06F3/0679 (No explanation available)
- Count: 340 patents
- Example: 20240231610. CLUSTER NAMESPACE FOR A MEMORY DEVICE (Micron Technology, Inc.)
- A61K45/06 (No explanation available)
- Count: 329 patents
- Example: 20240226036. 2-S RIMANTADINE AND 2-R RIMANTADINE FOR TREATING CANCER (Toragen, Inc.)
- H04L5/0051 (No explanation available)
Top Companies in Cybersecurity
QUALCOMM Incorporated
- Number of Cybersecurity patents: 1823
- Top CPC codes:
- H04W24/10 (No explanation available): 155 patents
- H04L5/0051 (No explanation available): 140 patents
- H04L5/0048 (No explanation available): 108 patents
- Recent patents:
- 20240049308. SYNCHRONOUS CHANNEL ACCESS CONTROL OF A WIRELESS SYSTEM (QUALCOMM Incorporated) (20240208)
- 20240049335. MANAGEMENT OF ANTENNA SWITCHING ACCORDING TO A SOUNDING REFERENCE SYMBOL ANTENNA SWITCHING CONFIGURATION (QUALCOMM Incorporated) (20240208)
- 20240049340. SMALL DATA TRANSMISSION OF NON-ACCESS STRATUM (NAS) MESSAGES AND UPLINK (UL) USER DATA PACKETS DURING A RADIO RESOURCE CONTROL (RRC) INACTIVE STATE (QUALCOMM Incorporated) (20240208)
Capital One Services, LLC
- Number of Cybersecurity patents: 635
- Top CPC codes:
- G06N20/00 (No explanation available): 82 patents
- G06Q20/4016 (No explanation available): 31 patents
- G06Q20/352 (No explanation available): 27 patents
- Recent patents:
- 20240046669. SYSTEMS AND METHODS FOR EXTRACTING IN-VIDEO MOVING TEXT IN LIVE VIDEO STREAMS (Capital One Services, LLC) (20240208)
- 20240048513. SYSTEMS AND METHODS FOR CONVERTING PHYSICAL MEETINGS INTO VIRTUAL MEETINGS (Capital One Services, LLC) (20240208)
- 20240048656. SELECTING A TARGET QUEUE FOR AN ELECTRONIC COMMUNICATION (Capital One Services, LLC) (20240208)
Micron Technology, Inc.
- Number of Cybersecurity patents: 631
- Top CPC codes:
- G06F3/0679 (No explanation available): 145 patents
- G06F3/0659 (No explanation available): 101 patents
- G06F3/0604 (No explanation available): 74 patents
- Recent patents:
- 20240047424. SEMICONDUCTOR DIES INCLUDING RECESSES FOR FACILITATING MECHANICAL DEBONDING, AND ASSOCIATED SYSTEMS AND DEVICES (Micron Technology, Inc.) (20240208)
- 20240047634. VERTICAL SOLID-STATE TRANSDUCERS HAVING BACKSIDE TERMINALS AND ASSOCIATED SYSTEMS AND METHODS (Micron Technology, Inc.) (20240208)
- 20240048788. INTELLIGENT INTERACTIVE VIDEO CONTENT BASED ON CONTEXTUAL AWARENESS FOR MOBILE APPLICATIONS (Micron Technology, Inc.) (20240208)
Apple Inc.
- Number of Cybersecurity patents: 563
- Top CPC codes:
- G06F3/013 (No explanation available): 45 patents
- G06F3/0482 (No explanation available): 29 patents
- G06F3/0488 (No explanation available): 27 patents
- Recent patents:
Dell Products L.P.
- Number of Cybersecurity patents: 561
- Top CPC codes:
- G06F2201/84 (No explanation available): 24 patents
- G06F3/067 (No explanation available): 23 patents
- G06F11/1451 (No explanation available): 23 patents
- Recent patents:
- 20240029462. METHOD AND SYSTEM FOR PREPROCESSING DIGITAL DOCUMENTS FOR DATA EXTRACTION (Dell Products L.P.) (20240125)
- 20240031542. INFORMATION HANDLING SYSTEM CAMERA VISUAL IMAGE COLOR TUNING BASED ON SENSED AMBIENT LIGHT COLOR (Dell Products L.P.) (20240125)
- 20240045981. SYSTEM AND METHOD FOR FILE RECOVERY FROM MALICIOUS ATTACKS (Dell Products L.P.) (20240208)
Microsoft Technology Licensing, LLC
- Number of Cybersecurity patents: 464
- Top CPC codes:
- G06N20/00 (No explanation available): 24 patents
- G06F40/40 (No explanation available): 20 patents
- G06F9/45558 (No explanation available): 18 patents
- Recent patents:
- 20240048258. HARMONIC-ENHANCED IDENTIFICATION (ID) AND DEVICE RESOLUTION FOR FREQUENCY MODULATING COMMUNICATION (Microsoft Technology Licensing, LLC) (20240208)
- 20240048447. ASSIGNMENTS OF IOT DEVICE TYPES (Microsoft Technology Licensing, LLC) (20240208)
- 20240048615. Propagating Origin Information For Applications During Application Installation (Microsoft Technology Licensing, LLC) (20240208)
Google LLC
- Number of Cybersecurity patents: 441
- Top CPC codes:
- G06N20/00 (No explanation available): 25 patents
- G10L15/22 (No explanation available): 21 patents
- G06F3/0482 (No explanation available): 18 patents
- Recent patents:
Cisco Technology, Inc.
- Number of Cybersecurity patents: 425
- Top CPC codes:
- H04L63/20 (No explanation available): 28 patents
- H04L63/1425 (No explanation available): 19 patents
- H04L43/12 (No explanation available): 16 patents
- Recent patents:
- 20240048562. SPONSOR DELEGATION FOR MULTI-FACTOR AUTHENTICATION (Cisco Technology, Inc.) (20240208)
- 20240049048. TRAFFIC ENGINEERING IN 5G AND LTE CUPS ARCHITECTURE (Cisco Technology, Inc.) (20240208)
- 20240049133. RESTRICTED TARGET WAIT TIME INTERFERENCE DETECTION AND MANAGEMENT (Cisco Technology, Inc.) (20240208)
Samsung Electronics Co., Ltd.
- Number of Cybersecurity patents: 422
- Top CPC codes:
- H04W24/10 (No explanation available): 23 patents
- H04W72/232 (No explanation available): 23 patents
- H04W72/23 (No explanation available): 22 patents
- Recent patents:
- 20240049341. METHOD OF HANDLING ACTIVE TIME FOR SL COMMUNICATION (Samsung Electronics Co., Ltd.) (20240208)
- 20240049354. METHOD AND APPARATUS FOR LINK AND TRAFFIC LEVEL EPCS SETUP AND OPERATIONS (Samsung Electronics Co., Ltd.) (20240208)
- 20240049355. METHOD AND APPARATUS FOR OPERATION PARAMETER UPDATE FOR EPCS (Samsung Electronics Co., Ltd.) (20240208)
Intel Corporation
- Number of Cybersecurity patents: 405
- Top CPC codes:
- G06T1/20 (No explanation available): 20 patents
- G06F9/45558 (No explanation available): 19 patents
- G06F12/1408 (No explanation available): 14 patents
- Recent patents:
- 20240048543. ENCRYPTION ACCELERATION FOR NETWORK COMMUNICATION PACKETS (Intel Corporation) (20240208)
- 20240048727. METHOD AND SYSTEM OF LOW LATENCY VIDEO CODING WITH INTERACTIVE APPLICATIONS (Intel Corporation) (20240208)
- 20240049272. METHODS AND DEVICES FOR RADIO RESOURCE SCHEDULING IN RADIO ACCESS NETWORKS (Intel Corporation) (20240208)
New Companies in Cybersecurity (Last Month)
No new companies detected in the last month.
Emerging Technology Areas in Cybersecurity
- H05K7/20563 (No explanation available)
- Count: 1 patents
- Example: 20240049434. Liquid cooling high-density pluggable modules for a network element (Ciena Corporation)
- H05K7/20636 (No explanation available)
- Count: 1 patents
- Example: 20240049434. Liquid cooling high-density pluggable modules for a network element (Ciena Corporation)
- H05B2213/07 (No explanation available)
- Count: 1 patents
- Example: 20240049369. METHODS FOR POWER CYCLE SELECTION IN APPLIANCES (Haier US Appliance Solutions, Inc.)
- H05B1/0266 (No explanation available)
- Count: 1 patents
- Example: 20240049369. METHODS FOR POWER CYCLE SELECTION IN APPLIANCES (Haier US Appliance Solutions, Inc.)
- H04W28/00 (No explanation available)
- H04B3/03 (No explanation available)
- Count: 1 patents
- Example: 20240049209. Using Power Domain NOMA for Continuous Bandwidth Requests (Cox Communications, Inc.)
- H04W36/00695 (No explanation available)
- G01S1/68 (No explanation available)
- Count: 1 patents
- Example: 20240048943. TRACKING DEVICE PRESENCE DETECTION AND REPORTING BY ACCESS POINTS (Tile, Inc.)
- H04N5/347 (No explanation available)
- Count: 1 patents
- Example: 20240048858. VIRTUAL CHANNEL CONFIGURATION SESSION OF A CAMERA SENSOR (QUALCOMM Incorporated)
- G01N21/9515 (No explanation available)
Top Companies in Emerging Cybersecurity Technologies
- Haier US Appliance Solutions, Inc.: 2 patents
- Ciena Corporation: 2 patents
- QUALCOMM Incorporated: 1 patents
- Comcast Cable Communications, LLC: 1 patents
- Tile, Inc.: 1 patents
- Nokia Technologies OY: 1 patents
- Cox Communications, Inc.: 1 patents
- Hong Kong Applied Science and Technology Resrearch Institute Company Limited: 1 patents
Top Inventors in Cybersecurity
Tao LUO of San Diego CA (US)
- Number of Cybersecurity patents: 247
- Top companies:
- QUALCOMM Incorporated: 236 patents
- QUALCOMM INCORPORATED: 8 patents
- Qualcomm Incorporated: 2 patents
- Recent patents:
- 20240049029. TECHNIQUES TO FACILITATE GROUP-BASED REPORTS WITH REPETITION ON CONFIGURED FOR AT LEAST ONE CHANNEL MEASUREMENT RESOURCE SET (QUALCOMM Incorporated) (20240208)
- 20240049239. SDCI MTRP UNIFIED TCI ACTIVATION DESIGN (QUALCOMM Incorporated) (20240208)
- 20240049240. UL GRANT SELECTION BY UE (QUALCOMM Incorporated) (20240208)
Yan ZHOU of San Diego CA (US)
- Number of Cybersecurity patents: 144
- Top companies:
- QUALCOMM Incorporated: 136 patents
- Qualcomm Incorporated: 3 patents
- QUALCOMM INCORPORATED: 3 patents
- Recent patents:
- 20240048215. BEAM FAILURE DETECTION EVALUATION ON TWO TRANSMISSION CONFIGURATION INDICATOR STATES (QUALCOMM Incorporated) (20240208)
- 20240049029. TECHNIQUES TO FACILITATE GROUP-BASED REPORTS WITH REPETITION ON CONFIGURED FOR AT LEAST ONE CHANNEL MEASUREMENT RESOURCE SET (QUALCOMM Incorporated) (20240208)
- 20240049239. SDCI MTRP UNIFIED TCI ACTIVATION DESIGN (QUALCOMM Incorporated) (20240208)
Esmael Hejazi Dinan of McLean VA (US)
- Number of Cybersecurity patents: 123
- Top companies:
- Ofinno, LLC: 75 patents
- Comcast Cable Communications, LLC: 45 patents
- Comcast Cable Communicatiions, LLC: 1 patents
- Recent patents:
- 20240049192. TRANSMISSION AND RECEPTION CONFIGURATION AND SIGNALING (Comcast Cable Communications, LLC) (20240208)
- 20240049298. Multicarrier Communications Employing Time Alignment Timers (Comcast Cable Communications, LLC) (20240208)
- 20240049330. Determination of Power Control Parameters (Comcast Cable Communications, LLC) (20240208)
Xiaoxia ZHANG of San Diego CA (US)
- Number of Cybersecurity patents: 117
- Top companies:
- QUALCOMM Incorporated: 113 patents
- Qualcomm Incorporated: 2 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
- 20240048311. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN NON-CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated) (20240208)
- 20240048327. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated) (20240208)
- 20240049183. SIDELINK PREPARATION PROCEDURE TIME REDUCTION (QUALCOMM Incorporated) (20240208)
Junyi LI of Fairless Hills PA (US)
- Number of Cybersecurity patents: 110
- Top companies:
- QUALCOMM Incorporated: 106 patents
- Qualcomm Incorporated: 2 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
Muhammad Sayed Khairy ABDELGHAFFAR of San Jose CA (US)
- Number of Cybersecurity patents: 92
- Top companies:
- QUALCOMM Incorporated: 89 patents
- QUALCOMM INCORPORATED: 2 patents
- QUALCOM Incorporated: 1 patents
- Recent patents:
- 20240048308. CONFIGURATION AND INDICATION OF RESOURCES FOR PARTIAL FREQUENCY SOUNDING (QUALCOMM Incorporated) (20240208)
- 20240048321. TIME DOMAIN ORTHOGONAL COVER CODE FOR SOUNDING REFERENCE SIGNAL TRANSMISSIONS (QUALCOMM Incorporated) (20240208)
- 20240049241. TYPE 0 RESOURCE ALLOCATION IN SUB-BAND FULL-DUPLEX SLOTS (QUALCOMM Incorporated) (20240208)
Mostafa KHOSHNEVISAN of San Diego CA (US)
- Number of Cybersecurity patents: 90
- Top companies:
- QUALCOMM Incorporated: 87 patents
- QUALCOMM INCORPORATED: 3 patents
- Recent patents:
- 20240048311. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN NON-CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated) (20240208)
- 20240048321. TIME DOMAIN ORTHOGONAL COVER CODE FOR SOUNDING REFERENCE SIGNAL TRANSMISSIONS (QUALCOMM Incorporated) (20240208)
- 20240048327. TECHNIQUES FOR INTERPRETING DOWNLINK CONTROL INFORMATION (DCI) FIELDS IN CODEBOOK-BASED MULTI-PANEL DEPLOYMENTS WITH DYNAMIC PANEL SWITCHING (QUALCOMM Incorporated) (20240208)
Peter GAAL of San Diego CA (US)
- Number of Cybersecurity patents: 89
- Top companies:
- QUALCOMM Incorporated: 87 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
- 20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated) (20240208)
- 20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated) (20240208)
- 20240049255. CONFIGURATION OF MULTICAST RECEPTION AND MOBILITY FOR USER EQUIPMENT IN AN INACTIVE STATE (QUALCOMM Incorporated) (20240208)
Jing SUN of San Diego CA (US)
- Number of Cybersecurity patents: 87
- Top companies:
- QUALCOMM Incorporated: 83 patents
- Qualcomm Incorporated: 2 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
Ahmed ELSHAFIE of San Diego CA (US)
- Number of Cybersecurity patents: 81
- Top companies:
- QUALCOMM Incorporated: 78 patents
- QUALCOMM INCORPORATED: 3 patents
- Recent patents:
Alexandros MANOLAKOS of Escondido CA (US)
- Number of Cybersecurity patents: 69
- Top companies:
- QUALCOMM Incorporated: 63 patents
- QUALCOMM INCORPORATED: 6 patents
- Recent patents:
- 20240027562. DISTRIBUTED UNIT-CENTRAL UNIT-SERVER SIGNALING OF PER-SECTOR FEATURES FOR POSITIONING (QUALCOMM Incorporated) (20240125)
- 20240031006. BEAM TRAINING FOR COORDINATED RELAYING (QUALCOMM Incorporated) (20240125)
- 20240031978. MOBILITY ANALYTICS EXCHANGE BETWEEN NETWORK ENTITIES (QUALCOMM Incorporated) (20240125)
Ahmed Attia ABOTABL of San Diego CA (US)
- Number of Cybersecurity patents: 69
- Top companies:
- QUALCOMM Incorporated: 69 patents
- Recent patents:
- 20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated) (20240125)
- 20240049226. CONSIDERATIONS FOR OVERLAP BETWEEN DATA AND ENERGY HARVESTING (QUALCOMM Incorporated) (20240208)
- 20240049241. TYPE 0 RESOURCE ALLOCATION IN SUB-BAND FULL-DUPLEX SLOTS (QUALCOMM Incorporated) (20240208)
Hua Zhou of Vienna VA (US)
- Number of Cybersecurity patents: 69
- Top companies:
- Ofinno, LLC: 41 patents
- Comcast Cable Communications, LLC: 26 patents
- Comcast Cable Communicatiions, LLC: 1 patents
- Recent patents:
Hyoungsuk Jeon of Centreville VA (US)
- Number of Cybersecurity patents: 68
- Top companies:
- Ofinno, LLC: 43 patents
- Comcast Cable Communications, LLC: 24 patents
- Comcast Cable Communicatiions, LLC: 1 patents
- Recent patents:
Huilin XU of Temecula CA (US)
- Number of Cybersecurity patents: 68
- Top companies:
- QUALCOMM Incorporated: 67 patents
- Qualcomm Incorporated: 1 patents
- Recent patents:
- 20240324018. BEAM SELECTION FOR RANDOM ACCESS IN A HIERARCHICAL BEAM ARCHITECTURE (QUALCOMM Incorporated) (20240926)
- 20240049140. COLLISION HANDLING FOR WUS (QUALCOMM Incorporated) (20240208)
- 20240049232. JOINT ADAPTATION BETWEEN CONTROL CHANNELS AND OTHER CONFIGURATIONS (QUALCOMM Incorporated) (20240208)
Kevin Higgins of Reno NV (US)
- Number of Cybersecurity patents: 65
- Top companies:
- IGT: 65 patents
- Recent patents:
Ali Cagatay Cirik of Chantilly VA (US)
- Number of Cybersecurity patents: 63
- Top companies:
- Ofinno, LLC: 37 patents
- Comcast Cable Communications, LLC: 24 patents
- Comcast Cable Communicatiions, LLC: 1 patents
- Recent patents:
Wanshi CHEN of San Diego CA (US)
- Number of Cybersecurity patents: 61
- Top companies:
- QUALCOMM Incorporated: 58 patents
- QUALCOMM INCORPORATED: 2 patents
- Qualcomm Incorporated: 1 patents
- Recent patents:
Yu ZHANG of San Diego CA (US)
- Number of Cybersecurity patents: 61
- Top companies:
- QUALCOMM Incorporated: 52 patents
- QUALCOMM INCORPORATED: 9 patents
- Recent patents:
- 20240048214. TECHNIQUES FOR COMMUNICATING USING A RECONFIGURABLE SURFACE (QUALCOMM Incorporated) (20240208)
- 20240048308. CONFIGURATION AND INDICATION OF RESOURCES FOR PARTIAL FREQUENCY SOUNDING (QUALCOMM Incorporated) (20240208)
- 20240049015. TECHNIQUES FOR REPORTING CHANNEL STATE INFORMATION (QUALCOMM INCORPORATED) (20240208)
Sony AKKARAKARAN of Poway CA (US)
- Number of Cybersecurity patents: 60
- Top companies:
- QUALCOMM Incorporated: 55 patents
- QUALCOMM INCORPORATED: 4 patents
- Qualcomm Incorporated: 1 patents
- Recent patents:
- 20240031991. NETWORK INDICATION TO CONTROL SIDELINK BEAM SELECTION (QUALCOMM Incorporated) (20240125)
- 20240032061. DOWNLINK CONTROL INFORMATION BASED UNIFIED TRANSMISSION CONFIGURATION INDICATOR ACKNOWLEDGEMENT (QUALCOMM INCORPORATED) (20240125)
- 20240048175. COMB OFFSET HOPPING FOR SRS (QUALCOMM Incorporated) (20240208)
Hung Dinh LY of San Diego CA (US)
- Number of Cybersecurity patents: 59
- Top companies:
- QUALCOMM Incorporated: 54 patents
- QUALCOMM INCORPORATED: 5 patents
- Recent patents:
- 20240324025. RESOURCE MAPPING FOR RANDOM ACCESS REPETITIONS USING A SAME SPATIAL FILTER (QUALCOMM Incorporated) (20240926)
- 20240031897. PHYSICAL UPLINK SHARED CHANNEL REPETITIONS DURING HANDOVER (QUALCOMM Incorporated) (20240125)
- 20240048214. TECHNIQUES FOR COMMUNICATING USING A RECONFIGURABLE SURFACE (QUALCOMM Incorporated) (20240208)
Sarbajit K. Rakshit
- Number of Cybersecurity patents: 58
- Top companies:
- International Business Machines Corporation: 29 patents
- INTERNATIONAL BUSINESS MACHINES CORPORATION: 28 patents
- Maplebear Inc.: 1 patents
- Recent patents:
- 20240223857. PERFORMING CONTEXT BASED DELIVERY OF DIGITAL CONTENT (International Business Machines Corporation) (20240704)
- 20240152152. Collaborative Capability Enhancement Among Machines (International Business Machines Corporation) (20240509)
- 20240331025. DYNAMIC BIDDING IN VIRTUAL COLLABORATIVE DOMAIN (International Business Machines Corporation) (20241003)
Kyungmin Park of Vienna VA (US)
- Number of Cybersecurity patents: 58
- Top companies:
- Ofinno, LLC: 36 patents
- Comcast Cable Communications, LLC: 20 patents
- Comcast Cable Communicatiions, LLC: 1 patents
- Recent patents:
- 20240323868. Physical Channel Processing Capability for Multiple Transmission Reception Points (Ofinno, LLC) (20240926)
- 20240324046. Beam Management for Cells in Wireless Communications (Comcast Cable Communications, LLC) (20240926)
- 20240049070. Uplink Selection For Handover (Comcast Cable Communications, LLC) (20240208)
Srinivas YERRAMALLI of San Diego CA (US)
- Number of Cybersecurity patents: 57
- Top companies:
- QUALCOMM Incorporated: 57 patents
- Recent patents:
Tao Luo of San Diego CA (US)
- Number of Cybersecurity patents: 57
- Top companies:
- QUALCOMM Incorporated: 49 patents
- QUALCOMM INCORPORATED: 6 patents
- QUALCOMM lncorporated: 1 patents
- Recent patents:
- 20240032023. REFERENCE SIGNAL PORT ASSOCIATION DETERMINATION FOR SINGLE FREQUENCY NETWORK UPLINK (QUALCOMM Incorporated) (20240125)
- 20240049088. MOBILITY OPTIMIZATION FOR NETWORK ENERGY SAVING (QUALCOMM Incorporated) (20240208)
- 20240049269. WAVEFORM-SPECIFIC TRANSMISSION PARTS (QUALCOMM Incorporated) (20240208)
Dawei Zhang of Saratoga CA (US)
- Number of Cybersecurity patents: 57
- Top companies:
- Apple Inc.: 46 patents
- APPLE INC.: 9 patents
- Apple Inc: 1 patents
- Recent patents:
Alberto RICO ALVARINO of San Diego CA (US)
- Number of Cybersecurity patents: 57
- Top companies:
- QUALCOMM Incorporated: 56 patents
- QUALCOMM INCORPORATED: 1 patents
- Recent patents:
- 20240049062. GROUP HANDOVER CONFIGURATIONS (QUALCOMM Incorporated) (20240208)
- 20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated) (20240208)
- 20240049255. CONFIGURATION OF MULTICAST RECEPTION AND MOBILITY FOR USER EQUIPMENT IN AN INACTIVE STATE (QUALCOMM Incorporated) (20240208)
Shan LIU of San Jose CA (US)
- Number of Cybersecurity patents: 56
- Top companies:
- Tencent America LLC: 44 patents
- TENCENT AMERICA LLC: 12 patents
- Recent patents:
- 20240031577. MOTION VECTOR PREDICTION FUSION FOR SUBBLOCK-BASED TEMPORAL MOTION VECTOR PREDICTION (SbTMVP) AND TEMPORAL MOTION VECTOR PREDICTION (TMVP) (TENCENT AMERICA LLC) (20240125)
- 20240031592. TEMPORAL MOTION VECTOR PREDICTOR WITH DISPLACEMENT (TENCENT AMERICA LLC) (20240125)
- 20240031594. METHOD AND APPARATUS FOR INTER PREDICTION MODE DEPENDENT SCALING FACTORS (TENCENT AMERICA LLC) (20240125)
Hao XU
- Number of Cybersecurity patents: 54
- Top companies:
- QUALCOMM Incorporated: 48 patents
- QUALCOMM INCORPORATED: 6 patents
- Recent patents:
- 20240048209. MULTI-MODE PRECODING MATRIX INFORMATION REPORT FOR ORBITAL ANGULAR MOMENTUM BASED COMMUNICATION SYSTEM (QUALCOMM Incorporated) (20240208)
- 20240049015. TECHNIQUES FOR REPORTING CHANNEL STATE INFORMATION (QUALCOMM INCORPORATED) (20240208)
- 20240049198. LATENCY REDUCTION TECHNIQUES IN WIRELESS COMMUNICATIONS (QUALCOMM Incorporated) (20240208)
Qian ZHANG of Basking Ridge NJ (US)
- Number of Cybersecurity patents: 54
- Top companies:
- QUALCOMM Incorporated: 52 patents
- Qualcomm Incorporated: 1 patents
- QUALCOM Incorporated: 1 patents
- Recent patents:
Fang YUAN
- Number of Cybersecurity patents: 54
- Top companies:
- QUALCOMM Incorporated: 49 patents
- QUALCOMM INCORPORATED: 4 patents
- QUALCOMM incorporated: 1 patents
- Recent patents:
- 20240032061. DOWNLINK CONTROL INFORMATION BASED UNIFIED TRANSMISSION CONFIGURATION INDICATOR ACKNOWLEDGEMENT (QUALCOMM INCORPORATED) (20240125)
- 20240032133. UNIFIED TRANSMISSION CONFIGURATION INDICATION FOR NONDEDICATED CHANNELS (QUALCOMM Incorporated) (20240125)
- 20240048215. BEAM FAILURE DETECTION EVALUATION ON TWO TRANSMISSION CONFIGURATION INDICATOR STATES (QUALCOMM Incorporated) (20240208)
Jeremy R. Fox of Georgetown TX (US)
- Number of Cybersecurity patents: 53
- Top companies:
- International Business Machines Corporation: 27 patents
- INTERNATIONAL BUSINESS MACHINES CORPORATION: 26 patents
- Recent patents:
- 20240331025. DYNAMIC BIDDING IN VIRTUAL COLLABORATIVE DOMAIN (International Business Machines Corporation) (20241003)
- 20240316465. MULTIPLAYER E-GAMING IMPORTABLE CONTROLS AND SETTINGS (INTERNATIONAL BUSINESS MACHINES CORPORATION) (20240926)
- 20240321270. VIRTUAL ASSISTANT NOTIFICATION AMELIORATION AND AWARENESS SYSTEMS AND METHODS (International Business Machines Corporation) (20240926)
- Number of Cybersecurity patents: 52
- Top companies:
- QUALCOMM Incorporated: 50 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
Linhai HE of San Diego CA (US)
- Number of Cybersecurity patents: 52
- Top companies:
- QUALCOMM Incorporated: 50 patents
- Qualcomm Incorporated: 1 patents
- QUALCOMM INCORPORATED: 1 patents
- Recent patents:
- 20240333405. CONFIGURATION AND PROCEDURE FOR SEARCH SPACE USED IN SMALL DATA TRANSFER OVER PRE-CONFIGURED UPLINK RESOURCES (QUALCOMM Incorporated) (20241003)
- 20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated) (20240125)
- 20240049232. JOINT ADAPTATION BETWEEN CONTROL CHANNELS AND OTHER CONFIGURATIONS (QUALCOMM Incorporated) (20240208)
Kapil GULATI of Belle Mead NJ (US)
- Number of Cybersecurity patents: 49
- Top companies:
- QUALCOMM Incorporated: 43 patents
- Qualcomm Incorporated: 3 patents
- QUALCOMM INCORPORATED: 3 patents
- Recent patents:
Wooseok NAM of San Diego CA (US)
- Number of Cybersecurity patents: 47
- Top companies:
- QUALCOMM Incorporated: 45 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
Chunxuan Ye of San Diego CA (US)
- Number of Cybersecurity patents: 44
- Top companies:
- Apple Inc.: 28 patents
- APPLE INC.: 9 patents
- InterDigital Patent Holdings, Inc.: 5 patents
- Recent patents:
- 20240031079. METHODS FOR MULTI-PDSCH TRANSMISSION WITH MULTIPLE PUCCH RESOURCES (APPLE INC.) (20240125)
- 20240049215. Scheduling Request (SR) Enhancements for 5G Real-Time Extended Reality (XR) Services (Apple Inc.) (20240208)
- 20240049223. Cancellation and Replacement of PUSCH (Apple Inc.) (20240208)
Abdelrahman Mohamed Ahmed Mohamed IBRAHIM of San Diego CA (US)
- Number of Cybersecurity patents: 44
- Top companies:
- QUALCOMM Incorporated: 43 patents
- QUALCOM Incorporated: 1 patents
- Recent patents:
- 20240322989. TECHNIQUES FOR SUB-BAND FULL-DUPLEX MODE AWARE COMMUNICATION (QUALCOMM Incorporated) (20240926)
- 20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated) (20240125)
- 20240049241. TYPE 0 RESOURCE ALLOCATION IN SUB-BAND FULL-DUPLEX SLOTS (QUALCOMM Incorporated) (20240208)
Ahmed Attia Abotabl of San Diego CA (US)
- Number of Cybersecurity patents: 43
- Top companies:
- QUALCOMM Incorporated: 43 patents
- Recent patents:
- 20240032001. FREQUENCY HOPPING IN FULL-DUPLEX COMMUNICATIONS (QUALCOMM Incorporated) (20240125)
- 20240048343. ADAPTATION OF A FIRST AVAILABLE RESOURCE BLOCK AND RESOURCE BLOCK GROUP SIZE FOR FULL-DUPLEX COMMUNICATIONS (QUALCOMM Incorporated) (20240208)
- 20240049002. MULTIPLE SEQUENCES OF NETWORK OPERATIONS FOR MULTIPLE TRANSMISSION AND RECEPTION POINTS (QUALCOMM Incorporated) (20240208)
Paul Marinier
- Number of Cybersecurity patents: 43
- Top companies:
- InterDigital Patent Holdings, Inc.: 39 patents
- INTERDIGITAL PATENT HOLDINGS, INC.: 4 patents
- Recent patents:
- 20240224320. SIMULTANEOUS UPLINK AND SIDELINK OPERATION (InterDigital Patent Holdings, Inc.) (20240704)
- 20240322979. METHODS FOR ULTRA-RELIABLE LOW-LATENCY COMMUNICATION MULTIPLEXING (INTERDIGITAL PATENT HOLDINGS, INC.) (20240926)
- 20240323922. SYSTEMS AND METHODS FOR SIDELINK COMMUNICATION (InterDigital Patent Holdings, Inc.) (20240926)
Marwen ZORGUI of San Diego CA (US)
- Number of Cybersecurity patents: 42
- Top companies:
- QUALCOMM Incorporated: 42 patents
- Recent patents:
- 20240323842. CELL WAKE-UP SIGNAL TRIGGERING AND RESOURCE SELECTION (QUALCOMM Incorporated) (20240926)
- 20240323891. POSITIONING MODEL CAPABILITY CONFIGURATION (QUALCOMM Incorporated) (20240926)
- 20240323988. CONFLICT RESOLUTION BETWEEN DATA TRANSMISSIONS AND NON-DATA SERVICE SIGNALS (QUALCOMM Incorporated) (20240926)
Joshua EDWARDS of Philadelphia PA (US)
- Number of Cybersecurity patents: 42
- Top companies:
- Capital One Services, LLC: 40 patents
- Capital One Servies, LLC: 1 patents
- Capital One Services,LLC: 1 patents
- Recent patents:
- 20240029142. METHODS AND SYSTEMS FOR ANONYMIZING AND PROVIDING ACCESS TO TRANSACTION DATA (Capital One Services, LLC) (20240125)
- 20240046270. INTELLIGENT DECISIONING AND ROUTING FOR REQUESTS RELATED TO AUTOMATED EVENTS (Capital One Services, LLC) (20240208)
- 20240046298. SYSTEMS AND METHODS FOR PROMOTING TRANSACTION REWARDS (Capital One Services, LLC) (20240208)
Jelena DAMNJANOVIC of Del Mar CA (US)
- Number of Cybersecurity patents: 42
- Top companies:
- QUALCOMM Incorporated: 42 patents
- Recent patents:
- 20240155719. UPLINK CHANNEL TRANSMISSIONS USING PER-TRANSMIT-RECEIVE-POINT-AND-PANEL POWER CONTROL PARAMETERS (QUALCOMM Incorporated) (20240509)
- 20240334399. SIDELINK BEAM MANAGEMENT BASED ON REFERENCE SIGNAL AND SIDELINK CHANNEL TRANSMISSIONS (QUALCOMM Incorporated) (20241003)
- 20240031895. JOINT TIMING ADVANCE AND CELL ACTIVATION SIGNALING (QUALCOMM Incorporated) (20240125)
Weimin DUAN of San Diego CA (US)
- Number of Cybersecurity patents: 40
- Top companies:
- QUALCOMM Incorporated: 38 patents
- QUALCOMM INCORPORATED: 2 patents
- Recent patents:
- 20240319359. RECONFIGURABLE INTELLIGENT SURFACE (RIS) AIDED ROUND-TRIP-TIME (RTT)-BASED USER EQUIPMENT (UE) POSITIONING (QUALCOMM Incorporated) (20240926)
- 20240027562. DISTRIBUTED UNIT-CENTRAL UNIT-SERVER SIGNALING OF PER-SECTOR FEATURES FOR POSITIONING (QUALCOMM Incorporated) (20240125)
- 20240031823. BEAM ADAPTATION FOR RECONFIGURABLE INTELLIGENT SURFACE AIDED UE POSITIONING (QUALCOMM Incorporated) (20240125)
Krishna Kiran MUKKAVILLI of San Diego CA (US)
- Number of Cybersecurity patents: 40
- Top companies:
- QUALCOMM Incorporated: 34 patents
- QUALCOMM INCORPORATED: 6 patents
- Recent patents:
- 20240032042. LOGICAL CHANNELS AND SCHEDULING REQUEST CONFIGURATIONS FOR FULL-DUPLEX MODES AND HALF-DUPLEX MODES (QUALCOMM Incorporated) (20240125)
- 20240048214. TECHNIQUES FOR COMMUNICATING USING A RECONFIGURABLE SURFACE (QUALCOMM Incorporated) (20240208)
- 20240048945. SELECTIVE TRIGGERING OF NEURAL NETWORK FUNCTIONS FOR POSITIONING MEASUREMENT FEATURE PROCESSING AT A USER EQUIPMENT (QUALCOMM Incorporated) (20240208)
Jeffrey RULE of Chevy Chase MD (US)
- Number of Cybersecurity patents: 40
- Top companies:
- Capital One Services, LLC: 40 patents
- Recent patents:
- 20240031477. MACHINE LEARNING DATASET GENERATION USING A NATURAL LANGUAGE PROCESSING TECHNIQUE (Capital One Services, LLC) (20240125)
- 20240045939. STEGANOGRAPHIC IMAGE ENCODING OF BIOMETRIC TEMPLATE INFORMATION ON A CARD (Capital One Services, LLC) (20240208)
- 20240046266. SYSTEMS AND METHODS FOR CRYPTOGRAPHIC CONTEXT-SWITCHING AUTHENTICATION BETWEEN WEBSITE AND MOBILE DEVICE (Capital One Services, LLC) (20240208)
Ahmed Elshafie of San Diego CA (US)
- Number of Cybersecurity patents: 40
- Top companies:
- QUALCOMM Incorporated: 35 patents
- QUALCOMM INCORPORATED: 4 patents
- Qualcomm Incorporated: 1 patents
- Recent patents:
Gabi SARKIS of San Diego CA (US)
- Number of Cybersecurity patents: 40
- Top companies:
- QUALCOMM Incorporated: 38 patents
- Qualcomm Incorporated: 1 patents
- QUALCOMM INCORPORATED: 1 patents
- Recent patents:
- 20240333585. RESOURCE SELECTION FOR SELF-CONTAINED INTER-USER-EQUIPMENT COORDINATION MESSAGE (QUALCOMM Incorporated) (20241003)
- 20240323893. SIDELINK POSITIONING ANCHOR CLASSIFICATION AND SELECTION (QUALCOMM Incorporated) (20240926)
- 20240031889. MODE 1 NETWORK ENTITY INITIATED NETWORK CODING HANDOVER (QUALCOMM Incorporated) (20240125)
Yushu Zhang
- Number of Cybersecurity patents: 38
- Top companies:
- Apple Inc.: 26 patents
- APPLE INC.: 12 patents
- Recent patents:
- 20240031096. SOLUTIONS FOR ENHANCEMENT OF INTER-CELL OPERATION FOR MULTI-TRP (APPLE INC.) (20240125)
- [[20240032054. ENHANCEMENT ON SCHEDULING AND HARQ-ACK FEEDBACK FOR URLLC, MULTIPLEXING SCHEME FOR CONTROL/DATA CHANNEL AND DM-RS FOR NR, AND ACTIVATION MECHANISM, SCHEDULING ASPECTS, AND SYNCHRONIZATION SIGNAL (SS) BLOCKS FOR NEW RADIO (NR) SYSTEM WITH MULTIPLE BANDWIDTH PARTS (BWPS) (Apple Inc.)]] (20240125)
- [[20240032055. ENHANCEMENT ON SCHEDULING AND HARQ-ACK FEEDBACK FOR URLLC, MULTIPLEXING SCHEME FOR CONTROL/DATA CHANNEL AND DM-RS FOR NR, AND ACTIVATION MECHANISM, SCHEDULING ASPECTS, AND SYNCHRONIZATION SIGNAL (SS) BLOCKS FOR NEW RADIO (NR) SYSTEM WITH MULTIPLE BANDWIDTH PARTS (BWPS) (Apple Inc.)]] (20240125)
Kazuki TAKEDA
- Number of Cybersecurity patents: 38
- Top companies:
- QUALCOMM Incorporated: 37 patents
- QUALCOMM INCORPORATED: 1 patents
- Recent patents:
- 20240048297. HYBRID AUTOMATIC REPEAT REQUEST PROCESS SPACE MANAGEMENT FOR MULTI-CELL SCHEDULING (QUALCOMM Incorporated) (20240208)
- 20240049254. DOWNLINK MULTICAST RECEPTION FOR INACTIVE MODE USER EQUIPMENT (QUALCOMM Incorporated) (20240208)
- 20240049255. CONFIGURATION OF MULTICAST RECEPTION AND MOBILITY FOR USER EQUIPMENT IN AN INACTIVE STATE (QUALCOMM Incorporated) (20240208)
Top Collaborations in Cybersecurity
Top US States for Cybersecurity Inventors
Top Cities for Cybersecurity Inventors
- San Diego: 6594 inventors
- San Jose: 3707 inventors
- San Francisco: 3459 inventors
- Beijing: 3087 inventors
- Bangalore: 2611 inventors
- Tokyo: 1882 inventors
- Shanghai: 1736 inventors
- New York: 1485 inventors
- Seattle: 1407 inventors
- Sunnyvale: 1323 inventors
- Shenzhen: 1272 inventors
- Austin: 1243 inventors
- Mountain View: 1232 inventors
- Cambridge: 1159 inventors
- London: 1086 inventors
- Santa Clara: 1045 inventors
- Palo Alto: 999 inventors
- Suwon-si: 933 inventors
- Fremont: 882 inventors
- Seoul: 878 inventors